Info: Version 1.8.x is available.
Last modified: $Date: 2024-03-30 11:25:00 +0000 (Sat, 30 Mar 2024) $
This page describes basic operations needed for using TOMOYO Linux.
To initialize policy, run
| [root@tomoyo ~]# /usr/lib/ccs/init_policy --file-only-profile |
if you want to use only MAC for files, or
| [root@tomoyo ~]# /usr/lib/ccs/init_policy |
if you want to enable all MAC functionalities.
TOMOYO Linux's policy files will be saved in /etc/ccs/ directory.
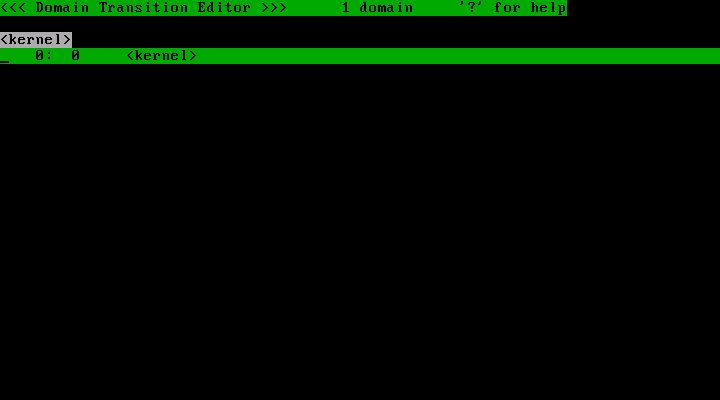
Run TOMOYO Linux's policy editor "ccs-editpolicy" with "/etc/ccs/" option, and you will see a picture shown below.
| [root@tomoyo ~]# /usr/sbin/ccs-editpolicy /etc/ccs/ |

This picture describes the domain tree. As of now, only "<kernel>" domain is defined. But as the system runs, TOMOYO Linux will create domains and add them to the tree. The example picture shown below has many domains.
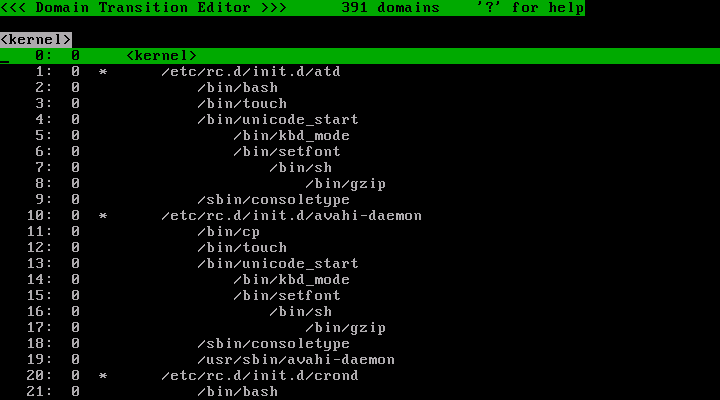
The MAC in TOMOYO Linux is applied in the units of domains. Every process belongs to single domain, and basically the process will transit to different domain whenever it executes a program. The name of a domain is a concatenated string expression for the process execution history. For example, the name of domain which the kernel belongs to is "<kernel>", the name of domain which /sbin/init invoked by the kernel belongs to is "<kernel> /sbin/init", the name of domain which /etc/rc.d/rc invoked by the /sbin/init belongs to is "<kernel> /sbin/init /etc/rc.d/rc". The exceptions of this transition rule are described later.
Look at the number which are the second column of each line.
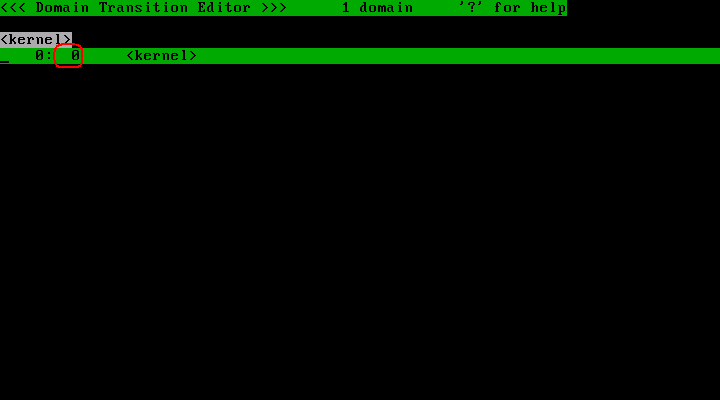
This number is called "profile number". A profile number is an integer value which takes between 0 and 255.
Press "w" key, and you will see some choices.
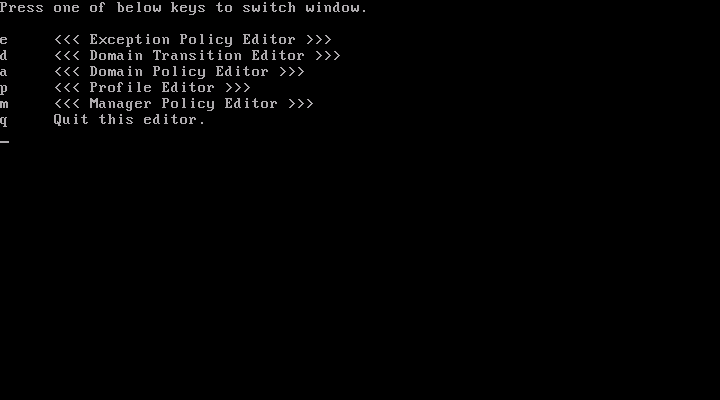
Press "p" key, and you will see the list of profiles.
If you gave "--file-only-profile" option when executing /usr/lib/ccs/init_policy , you will see entries shown in below picture.
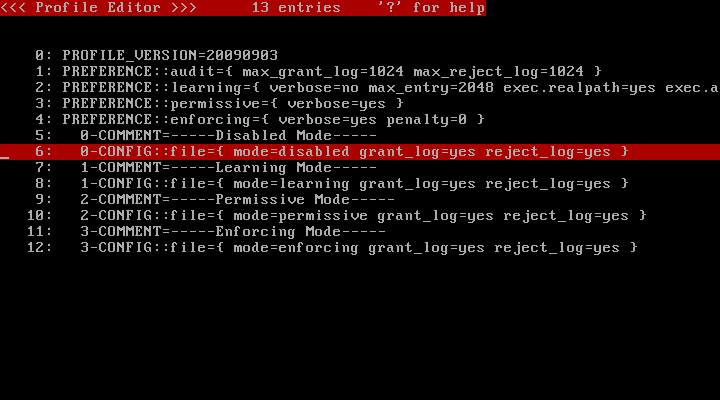
If you didn't give "--file-only-profile" option when executing /usr/lib/ccs/init_policy , you will see entries shown in below picture.
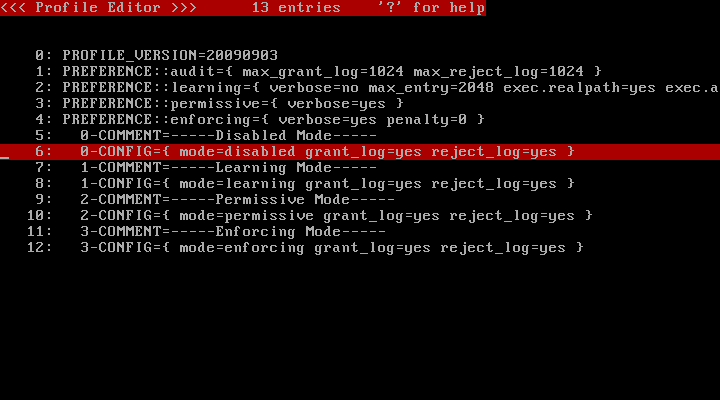
| Name | Control |
| PREFERENCE::audit | Configuration of auditing preference. |
| PREFERENCE::learning | Configuration of learning mode. |
| PREFERENCE::permissive | Configuration of permissive mode. |
| PREFERENCE::enforcing | Configuration of enforcing mode. |
| COMMENT | A line of text that describes the content of the profile. |
| CONFIG | Configuration of Mandatory Access Control(MAC) level. |
You can give the following values for verbose= parameter of PREFERENCE::learning PREFERENCE::permissive PREFERENCE::enforcing .
| Value | Meaning |
| no | Don't dump policy violation messages. |
| yes | Dump policy violation messages. |
You can give the following values for mode= parameter of CONFIG line.
| Value | Meaning |
| disabled | Disabled. Works as if regular kernel. |
| learning | Learning mode. Not rejected if the request violates policy. Automatically appended to policy. |
| permissive | Permissive mode. Not rejected if the request violates policy. Not appended to policy automatically. |
| enforcing | Enforcing mode. Rejected if the request violates policy. |
Press "w" key, then press "e" key, and you will see the picture shown below.
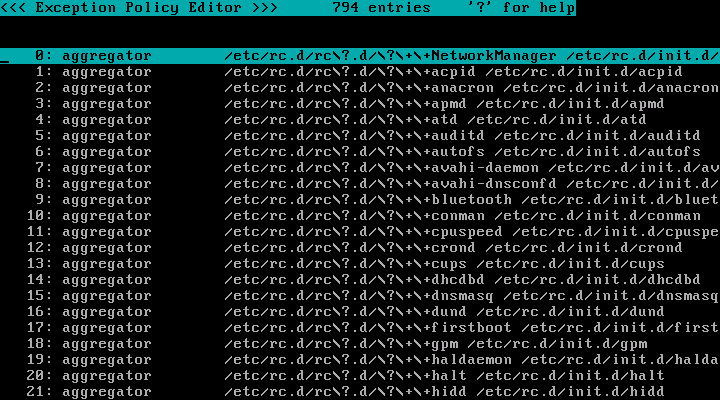
You can scroll this window using arrow keys and/or Home/End/PageUp/PageDown keys.
This screen contains the following types of exceptions.
| (1) Pathname pattern |
Register pathnames with patterns using the "file_pattern" directive. When a file operation is performed and the requested pathname matches a patterned pathname registered with "file_pattern" directive, policy is generated using patterned pathnames.
TOMOYO Linux needs more patterned pathnames depending on the applications installed and their configurations. You can add missing patterned pathnames after running the system. | ||
| (2) Pathname group |
Register pathname groups using the "path_group" directive. This is a macro to reduce the amount of domain policy by grouping multiple pathnames using group names. An example usage is shown later. | ||
| (3) Number group |
Register number groups using the "number_group" directive. This is a macro to reduce the amount of domain policy by grouping multiple numbers using group names. An example usage is shown later. | ||
| (4) Address group |
Register IPv4 or IPv6 address groups using the "address_group" directive. This is a macro to reduce the amount of domain policy by grouping multiple addresses using group names. An example usage is shown later. | ||
| (5) Unconditionally readable files |
Register files that are allowed to be read by all programs using the "allow_read" directive. Patterns are allowed. When a file open request for reading is issued and the requested pathname matches a pathname registered with "allow_read" directive, the open request for read access is granted even if the pathname is not explicitly permitted by the domain policy.
You may find more files depending on applications in your system or configurations. Add missing files after observing which files are used for read access. | ||
| (6) Unconditionally usable environment variable names |
Register environment variable names that are allowed to be passed to all programs using the "allow_env" directive. Patterns are allowed. When execve() request is issued and the passed environment variable name matches matches environment variable names registered with "allow_env" directive, the environment variable name is granted without checking domain policy.
You may find more environment variable names depending on applications in your system or configurations. Add missing environment variable names after observing which environment variable names are used. | ||
| (7) Non-rewritable files |
Register files that you don't want to allow overwriting existing contents (like log files) using "deny_rewrite" directive. Patterns are allowed. Files registered with "deny_rewrite" directive are (as long as it is not explicitly given by "allow_rewrite" directive in domain policy) forbidden to "open for writing but not append mode" and "truncate".
You may find more files depending on applications in your system or configurations. Add missing files after observing which files are used for append-only access. | ||
| (8) Program aggregations |
To deal multiple programs as a single program, use aggregator directive followed by name of original program and aggregated program. Patterns are allowed for name of original program. | ||
| (9) Programs that cause domain transition initialization |
Register programs that initializes the domain transition history using the "initialize_domain" directive. No patterns allowed. When a program that is registered with "initialize_domain" directive is executed, the program runs just under the <kernel> domain.
You may find more programs depending on applications in your system or configurations. Add missing programs after observing which programs should be initialize their domain transition history. But be careful with the side effect of other domains. For example, when the domain policy already includes
and you add /bin/tcsh as initialize_domain, "<kernel> ... /bin/bash /bin/tcsh" will become unreachable domain because /bin/tcsh runs in "<kernel> /bin/tcsh" domain. In that case, you will need to replace "<kernel> ... /bin/bash /bin/tcsh" with "<kernel> /bin/tcsh" as shown below.
| ||
| (10) Programs that prevent domain transition initialization |
To deny the effect of "initialize_domain" directive under specific conditions, use "no_initialize_domain" directive. | ||
| (11) Domains that prevent domain transition |
To declare domain keepers, use "keep_domain" directive followed by domain definition. | ||
| (12) Domains that cause domain transition |
To deny the effect of "keep_domain" directive under specific conditions, use "no_keep_domain" directive. | ||
| (13) Reserved local ports |
To reserve local ports, use "deny_autobind" directive followed by port number. |
Press "q" key to finish the policy editor.
Please see the policy editor's tutorial page How to use Policy Editor as needed.
TOMOYO Linux can record "access granted logs" (access requests that didn't violate domain policy) and "access rejected logs" (access requests that violated domain policy).
The logs are in the form of domain policy so that the logs can be directly appended to domain policy. Add the "access rejected logs" to domain policy if you consider you should allow the access.
You can use a daemon program that reads from /proc/ccs/grant_log and /proc/ccs/reject_log and writes to files. Run in the following way from (for example) /etc/rc.local .
| /usr/sbin/ccs-auditd $location_to_store_access_granted_logs $location_to_store_access_rejected_logs |
You may give PREFERENCE::audit={ max_grant_log=0 } for profiles and give /dev/null for $location_to_store_access_granted_logs if you don't want "access granted logs". Since "ccs-auditd" doesn't have filtering functions, be careful with the disk's free space if you want to save "access granted logs".
You may give PREFERENCE::audit={ max_reject_log=0 } for profiles and give /dev/null for $location_to_store_access_rejected_logs if you don't want "access rejected logs". But I recommend you to save "access rejected logs". This manual assumes that "access rejected logs" is saved in /var/log/tomoyo/reject_log.conf .
| /usr/sbin/ccs-auditd /dev/null /var/log/tomoyo/reject_log.conf |
Create directories manually for storing access logs.
| [root@tomoyo ~]# mkdir -p /var/log/tomoyo |
If you want to rotate using "logrotate", create /etc/logrotate.d/tomoyo with the following content. Be sure to give "nocreate" option, or logs after the first rotation will not be saved.
|
/var/log/tomoyo/reject_log.conf { weekly rotate 9 missingok notifempty nocreate } |
If you don't want neither "access granted logs" nor "access rejected logs", you needn't to run "ccs-auditd" and you can give PREFERENCE::audit={ max_grant_log=0 max_reject_log=0 } for profiles to save memory and improve performance.
TOMOYO Linux can report the occurrence of policy violation in enforcing mode, if you have set up a mean to notify (e.g. mail).
You can use cron daemon for notifying. For example, to notify root@example.com via mail, once per an hour, add
| 00 * * * * root /usr/lib/ccs/ccs-notifyd 0 'mail root@example.com' |
to /etc/crontab .
Now, reboot with TOMOYO Linux kernel.
| [root@tomoyo ~]# reboot |