Info: Version 1.8.x is available.
Last modified: $Date: 2024-03-31 15:45:12 +0000 (Sun, 31 Mar 2024) $
TOMOYO Linux is a secure OS developed by NTT DATA Corporation, Japan, and was released on November 2005 under the GPL. Some portion of TOMOYO Linux's functionality is integrated into Linux kernel 2.6.30 released on June 2009. Technical information is available at project page at SourceForge. This series aims at actually experiencing and mastering TOMOYO Linux. Please stay with me.
I explain summary of secure OS and steps for introducing TOMOYO Linux. I explain steps for installing TOMOYO Linux 1.7.4 running on CentOS 5 installed on VMware environment. Also, I explain steps for booting with TOMOYO Linux kernel and experiencing TOMOYO Linux's automatic policy learning mode.
Generally, secure OS is explained as OS with mandatory access control and least privilege functionalities. Both functionalities are intended for restricting exercise of functionalities provided by OS. The author of this series considers secure OS as "negative technologies", for secure OS is for "reducing what you can do with OS" rather than "increasing functionality or what you can do with OS". Also, secure OS entails "works and burdens for reducing what you can do with OS" as an unhappy bonus. Why dare to spend time and effort for reducing what you can do with OS? The reason is for enhancing security. In normal OS (in other words, OS without mandatory access control and least privilege functionalities), general versatility does you an ill office if the OS once lost control by unauthorized access. For example, public WWW servers published to the web should be able to provide only WWW service and should not be able to provide other services. Secure OS is used for restricting services which was originally designed for generic services. (Fig. 1 and Fig. 2)
♦ Fig. 1 Access is free on normal OS
|
♦ Fig. 2 Access is restricted according to policy on secure OS
|
The "restriction" is mainly implemented as reinforcement of access controls. This reinforced access control is so-called MAC (Mandatory Access Control) system. Computer systems itself cannot determine what operations should be permitted and what shouldn't be. Thus, to use the MAC system, you have to tell the MAC system what operations should be permitted and what shouldn't be. The definition of what operations should be permitted and what shouldn't be is called "policy". Therefore, using secure OS entails burden of managing policy. The importance of security is increasing day by day. Nonetheless, why does secure OS remain unfamiliar? There are several factors that keep secure OS away, but the largest factor would be "the concept of secure OS is difficult and management of policy is very complicated". I don't explain the difficulty in details, but writing policy is not an easy task even for experienced and skilled Linux administrators.
TOMOYO Linux adopted an approach "OS by itself generates policy" in order to solve the fundamental issue of secure OS's policy management and realized "secure OS with practically manageable level". Regarding TOMOYO Linux, you can start using TOMOYO Linux from the first day if you have experience of installing and administrating Linux. In the first installment of this series, I explain from introducing TOMOYO Linux till using automatic policy learning mode for generating elementary policy. There is nothing difficult. Please actually operate and experience the new world by TOMOYO Linux.
TOMOYO Linux supports Linux kernel 2.4.37 and 2.6.27 to 2.6.37 and some distribution's latest kernels.
In this series, I explain using CentOS 5 as an example, but you can do in a similar manner for any distributions.
See Installing TOMOYO Linux kernels and tools. for how to download and install kernel and tools.
Utility programs are installed into /usr/sbin/ directory. Role of each program is described in Fig. 7. I explain usage of these programs when each program appears for the first time in this series.
♦ Fig. 7 Programs for managing TOMOYO Linux
|
Add the location of TOMOYO Linux's utility programs to environment variable PATH. Append a line in Fig. 8 to ~/.bashrc if you are using /bin/bash .
♦ Fig. 8 Updating environment variable PATH
export PATH=$PATH:/usr/sbin |
In TOMOYO Linux, any requests that are not granted by policy are rejected. Thus, all requests that are needed for operating the system properly have to be explicitly granted by policy. But to make the policy compact, TOMOYO Linux has a notion called "exception policy".
You will refine the content of exception policy as you develop policy. You can generate initial exception policy by running command in Fig. 9.
♦ Fig. 9 Initializing policy configuration
# /usr/lib/ccs/init_policy Creating policy directory... OK Creating exception policy... OK Creating domain policy... OK Creating manager policy... OK Creating default profile... OK Creating memory quota policy... OK Creating module loader... OK |
To control how access is restricted, TOMOYO Linux has a notion called "profile". I explain the details on profiles and steps for controlling profiles in future installments.
Although /etc/ccs/profile.conf was generated by previously executed init_policy command, overwrite that file with the contents listed in Fig. 10 for this installment. The first line is profile's version, the second line is "set access control mode of files to learning mode".
♦ Fig. 10 Contents of /etc/ccs/profile.conf
PROFILE_VERSION=20090903
0-CONFIG::file={ mode=learning }
|
Now you have finished all preparation. You can't wait any more?
Reboot the system using reboot command. (Fig. 11)
♦ Fig. 11 Rebooting the system
# reboot |
Choose the entry with TOMOYO Linux kernel at the GRUB screen which will be displayed upon reboot. (Fig. 12)
♦ Fig. 12 Choosing TOMOYO Linux kernel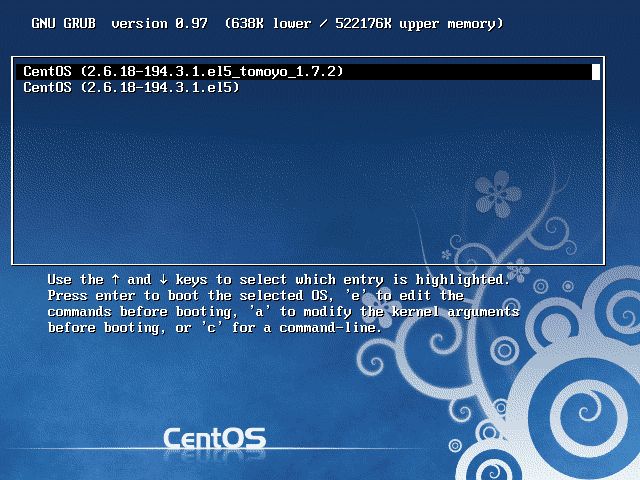
|
If you operated properly, TOMOYO Linux will boot in "learning mode". (Fig. 13)
♦ Fig. 13 Booting with TOMOYO Linux kernel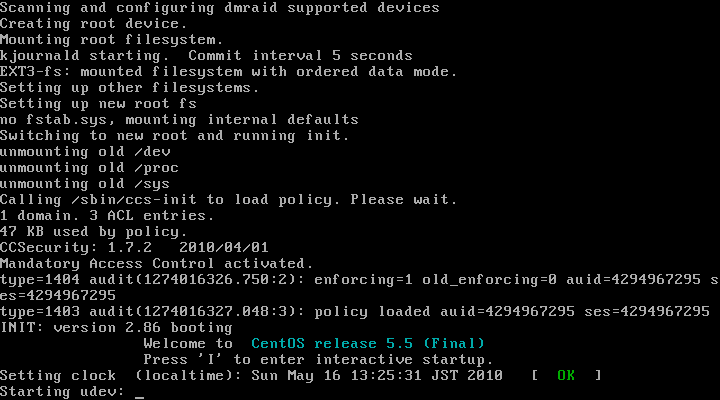
|
If your system cannot boot due to TOMOYO Linux, you can boot your system with TOMOYO Linux disabled by appending ccsecurity=off at the kernel's command line parameters.
TOMOYO Linux does not require modification against existing Linux libraries and applications. Thus, uninstalling TOMOYO Linux is quite easy. If you want to uninstall TOMOYO Linux by some reason, the system will become normal Linux by removing /sbin/ccs-init (a program which loads policy when /sbin/init starts). If you want to uninstall TOMOYO Linux kernel in addition to /sbin/ccs-init , reboot with normal kernel and uninstall the TOMOYO Linux kernel package using rpm command.
In TOMOYO Linux, access control is applied in the unit of "domain". Every process belongs to one domain, and basically transits to different domain whenever a program is executed. (Fig. 14)
♦ Fig. 14 Domain transition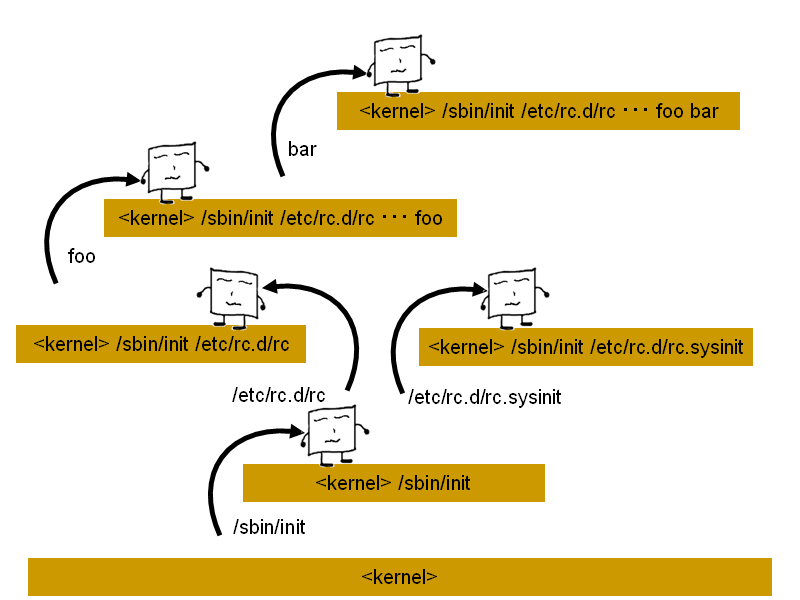
|
The domain in TOMOYO Linux is the string representation of concatenation of process's execution history starting from <kernel>. For example, domain for "the kernel process" is "<kernel>", domain for "/sbin/init executed by the kernel process" is "<kernel> /sbin/init", domain for "/etc/rc.d/rc executed by /sbin/init" is "<kernel> /sbin/init /etc/rc.d/rc".
Now, let's browse the policy obtained by TOMOYO Linux's learning mode. TOMOYO Linux has CUI policy editor. Please login as root user and run ccs-editpolicy command. (Fig. 15. Error messages will be printed if you didn't choose TOMOYO Linux kernel at Fig. 12)
♦ Fig. 15 Executing policy editor
# /usr/sbin/ccs-editpolicy |
The policy editor has several functionalities. Default initial mode is "<<< Domain Transition Editor >>>". (Fig. 16) The first line of the screen is for title area, the second line is for message area, the third line is for printing domainname currently selected by cursor. Regarding the fourth and below lines, the first number is the line number, second number is the profile number (I explain about profile numbers in next installment). In Fig. 16, there are 342 domains defined. (The profile numbers and the number of domains vary on how you operated and how you configured.)
♦ Fig. 16 Initial screen of policy editor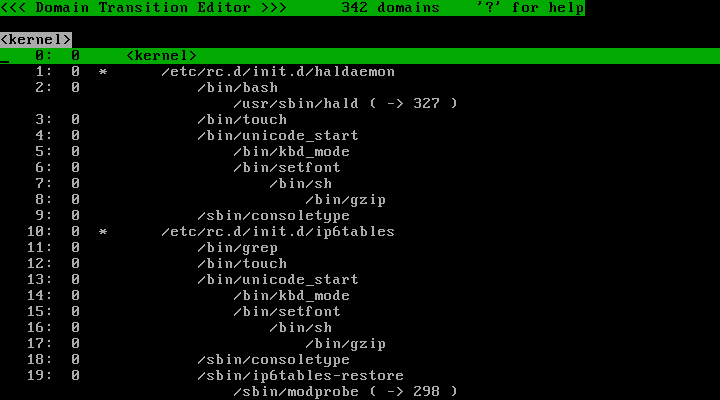
|
Let's browse the list of domains which TOMOYO Linux learned by scrolling with cursor keys. Fig. 17 shows domain transitions from /sbin/init . You can see that /etc/rc.d/rc is executed from /sbin/init and programs in /etc/rc.d/init.d/ directory are executed from /etc/rc.d/rc .
♦ Fig. 17 Domain for /sbin/init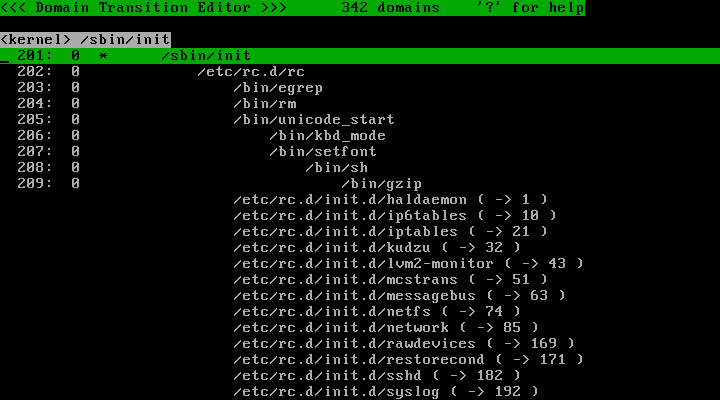
|
Now, as an example, let's browse the policy for domain for policy editor currently executing. By pressing "F" key, the cursor moves to the bottom line of screen and waits for input. Enter "ccs-editpolicy" and press "Enter" key, and you will see the cursor jumped to the domain for policy editor currently executing. (Fig. 18)
♦ Fig. 18 Domain for /usr/sbin/ccs-editpolicy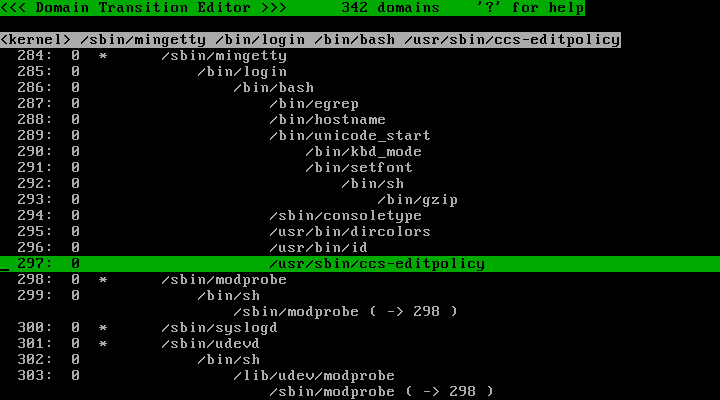
|
In Fig. 18, TOMOYO Linux identifies the domain for policy editor as "<kernel> /sbin/mingetty /bin/login /bin/bash /usr/sbin/ccs-editpolicy" ( /usr/sbin/ccs-editpolicy executed from /bin/bash executed from /bin/login executed from /sbin/mingetty ). ( TOMOYO Linux will identify the domain for policy editor as "<kernel> /usr/sbin/sshd /bin/bash /usr/sbin/ccs-editpolicy" if /usr/sbin/ccs-editpolicy is executed from /bin/bash executed from /usr/sbin/sshd .)
To browse permissions for this domain appended by learning mode, press "Enter" key. Then, you will see a screen like Fig. 19. The heading line changed from <<< Domain Transition Editor >>> to <<< Domain Policy Editor >>>. This screen shows permissions for "<kernel> /sbin/mingetty /bin/login /bin/bash /usr/sbin/ccs-editpolicy" domain and currently 7 entries are listed in this screen. Regarding the fourth and below lines, the first number is the line number. "allow_read/write" means "allow opening file for reading and writing". "allow_read" means "allow opening file for reading". "allow_ioctl" means "allow ioctl with specified command number".
♦ Fig. 19 Permissions given to domain for /usr/sbin/ccs-editpolicy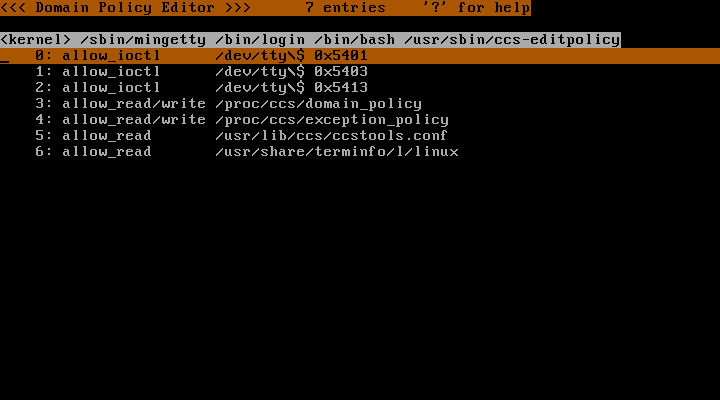
|
To return to domain transition editor's screen from this screen, press "Enter" key. To quit the policy editor, press "Q" key. ccs-editpolicy is an editor which directly edits policy currently in kernel's memory rather than policy files on disk. Thus, modification made by ccs-editpolicy is immediately reflected. You can monitor policy changes momentarily appended by learning mode.
Try executing various commands, and see how these commands are identified as domains by TOMOYO Linux, and see how TOMOYO Linux recorded files accessed by these commands. By repeating these operations for several times, you will be naturally able to understand TOMOYO Linux's domain management and learning mode and policy. This lucidity is the TOMOYO Linux's feature.
To browse currently running processes and domains which these processes belong to and profile number which these domains are assigned, run ccs-pstree command. Profile number and process's name and process's ID and domainname will be printed like pstree command. (Fig. 20)
♦ Fig. 20 List of domains for currently running processes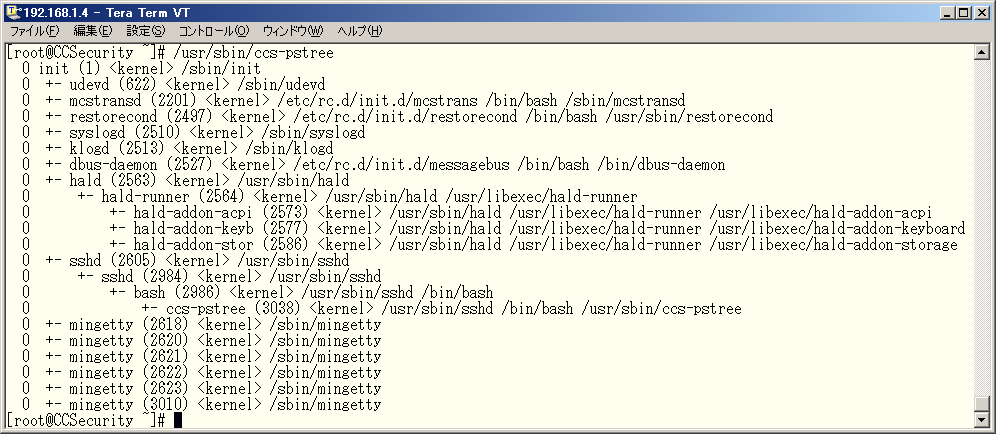
|
To save policy currently in kernel memory onto disk, run ccs-savepolicy command. (Fig. 21) Two files named exception_policy.conf and domain_policy.conf will be created in /etc/ccs/ directory by executing ccs-savepolicy command.
♦ Fig. 21 Saving policy in kernel memory into files on disk
# /usr/sbin/ccs-savepolicy |
Policy files in TOMOYO Linux are plain text files with filenames and directory names. To load policy files currently on disk, run ccs-loadpolicy command. (Fig. 22)
♦ Fig. 22 Loading policy files on disk into kernel memory
# /usr/sbin/ccs-loadpolicy af |
The "a" option means both exception_policy.conf and domain_policy.conf explained above, and "f" option means "freshen (overwrite)". If you didn't give "f" option, policy files in /etc/ccs/ directory will be appended to current policy in the kernel memory.
In this installment, I explained steps for installing TOMOYO Linux and steps for using automatic learning mode on files and steps for saving the learned result. In the next installment, I explain steps for restricting access based on policy. Don't miss it!
Proceed to the second installment.