Info: Version 1.8.x is available.
Last modified: $Date: 2024-03-30 11:25:00 +0000 (Sat, 30 Mar 2024) $
This page describes how to use TOMOYO Linux's learning mode.
After you rebooted the system with TOMOYO Linux kernels, login as root.
Decide what application to analyze/protect.
Below procedure is a case of Apache in CentOS 5 environment.
Start the target application.
| [root@tomoyo ~]# service httpd start |
Let's start TOMOYO Linux's policy editor. Please note that this time, you don't need to pass /etc/ccs/ to the command line, for we directly edits TOMOYO Linux's policy currently used by the kernel.
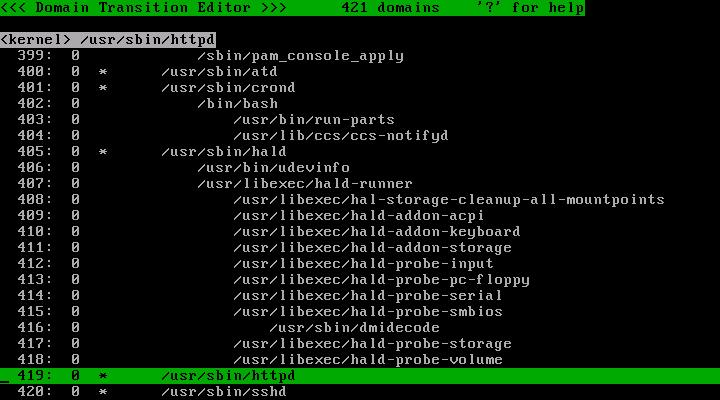
In the CentOS 5 , Apache's program's location is /usr/sbin/httpd .
Scroll the cursor using arrow-keys and/or Home/End/PageUp/PageDown keys to find the line /usr/sbin/httpd . In this picture, it is line 419.

If /usr/sbin/httpd is registered with "initialize_domain", a domain named "<kernel> /usr/sbin/httpd" is created by invoking /usr/sbin/httpd . If not registered, a child domain of invoker domain (for example, if you invoked from "<kernel> /usr/sbin/mingetty /bin/login /bin/bash", it is "<kernel> /usr/sbin/mingetty /bin/login /bin/bash /usr/sbin/httpd") is created. This manual assumes that /usr/sbin/httpd is registered with "initialize_domain".
Press 's' key and enter '1' and press 'Enter' key.
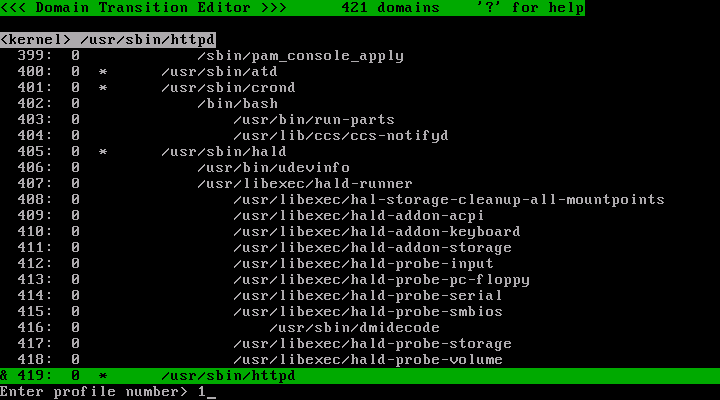
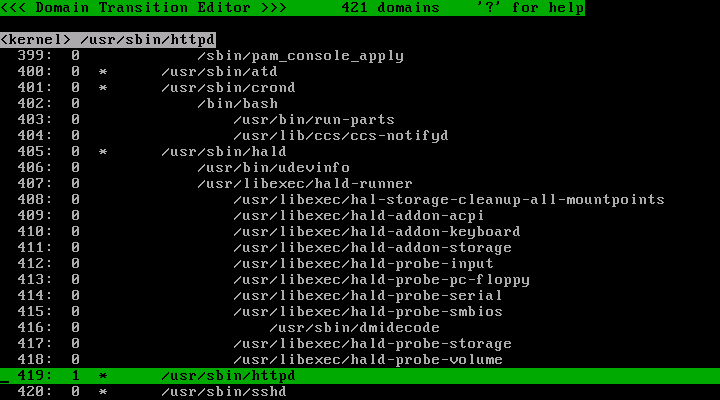
Now the profile number of the /usr/sbin/httpd has changed to 1.
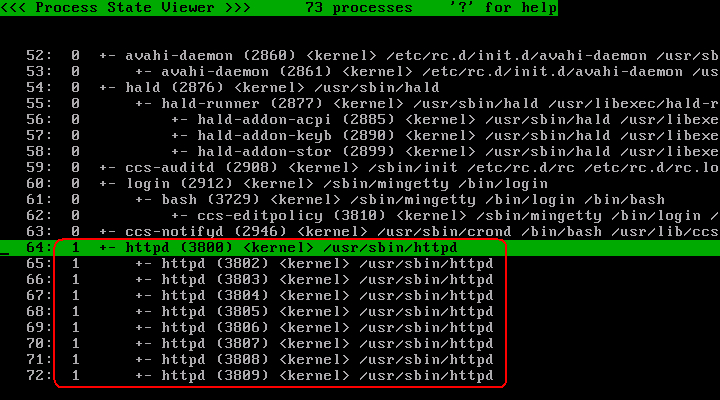
Press '@' key to switch to process list. Verify that /usr/sbin/httpd processes are assigned profile number 1.
Press 'q' key to quit the policy editor.
Restart the Apache in order to learn necessary permissions for starting/finishing the Apache.
| [root@tomoyo ~]# service httpd restart |
Run TOMOYO Linux's policy editor again and go to the /usr/sbin/httpd line. (Line number may be changed because new domains are added by programs executed by you and the system.)
Press 'Enter' key to browse the permissions gathered by now.
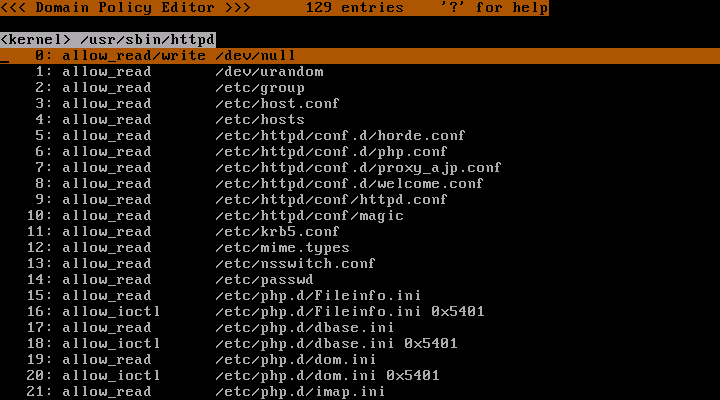
Press 'q' key to quit the policy editor. Do whatever you want to allow Apache.
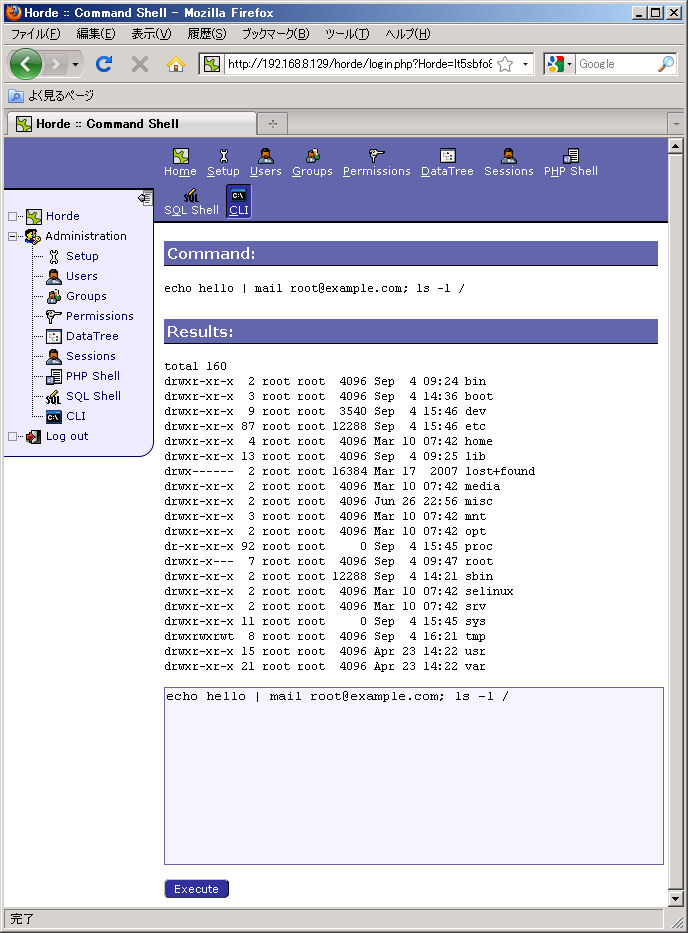
Be sure to sometimes save policy, for necessary permissions are accumulated on only kernel memory. If you reboot the system, all gathered permissions will be lost.
To save the policy currently in the kernel onto the disk, use "ccs-savepolicy" command.
| [root@tomoyo ~]# /usr/sbin/ccs-savepolicy |
By executing "ccs-savepolicy", two files ("exception_policy.conf", "domain_policy.conf") are created in the /etc/ccs/ directory. To be accurate, they are symbolic links to text files whose filenames contain the creation time.
To load the policy currently on the disk into the kernel, use "ccs-loadpolicy" command.
| [root@tomoyo ~]# /usr/sbin/ccs-loadpolicy af |
The "a" option means load two files ("exception_policy.conf", "domain_policy.conf"). The "f" option means erase the policy currently in the kernel before loading the policy currently on the disk. If "f" is not given, the policy currently on the disk will be added to the policy currently in the kernel.
After you came to think you have done roughly everything you want to allow Apache to do, run the policy editor and change the profile number to 2. Note that Apache may have executed some external programs (e.g. /bin/sh , /usr/bin/perl , /usr/lib/sendmail) and thus has descendant domains. Be sure to change the profile number for descendant domains if any as well as the /usr/sbin/httpd domain.
Choose target domains and press 's' key and enter '2' and press 'Enter' key.
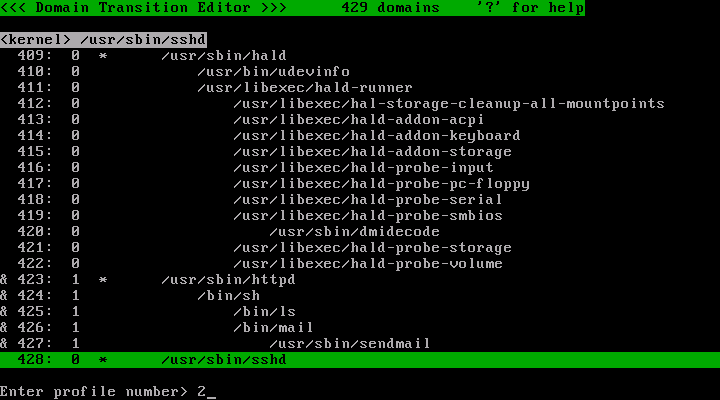
Now the profile number of the /usr/sbin/httpd and descendant has changed to 2.
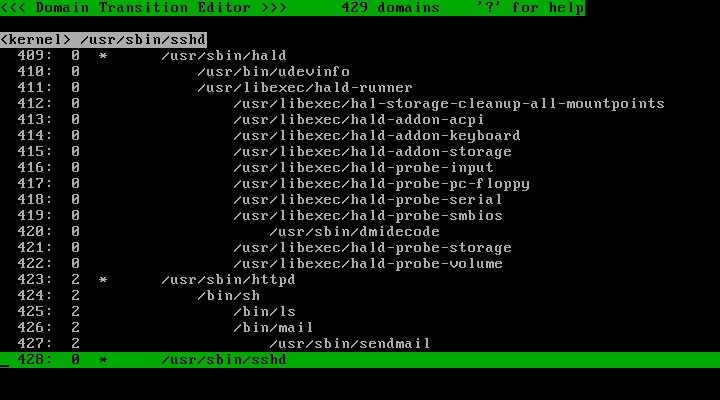
Press 'q' key to quit the policy editor. Redo whatever you want to allow Apache to do.
If the profile is configured as "PREFERENCE::permissive={ verbose=yes }" (this is default), the "WARNING:" messages will be printed to the console when policy violation occurs.
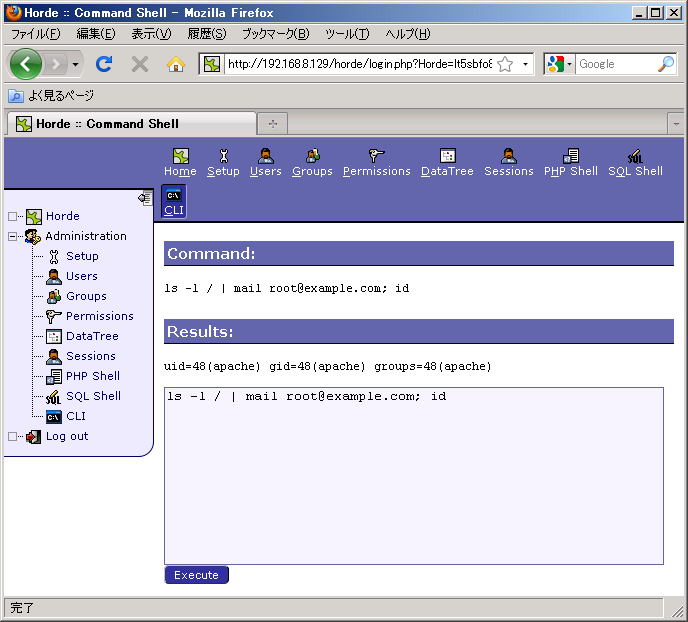
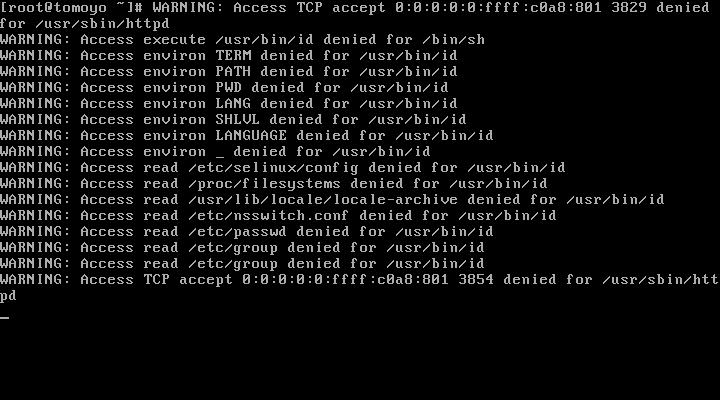
If you have configured audit logs at Phase 2: Initializing TOMOYO Linux., you can pick up necessary permissions from audit logs using "grep".
|
[root@tomoyo ~]# grep -A 3 -F 'profile=2 mode=permissive' /var/log/tomoyo/reject_log.conf #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=3039) task={ pid=3039 ppid=3034 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } <kernel> /usr/sbin/httpd allow_network TCP accept 0:0:0:0:0:ffff:c0a8:801 1507 #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=603159 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=589834 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=linux" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } } <kernel> /usr/sbin/httpd /bin/sh allow_execute /usr/bin/id #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=603159 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=589834 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=linux" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_env TERM #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=603159 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=589834 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=linux" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_env PATH #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=603159 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=589834 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=linux" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_env PWD #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=603159 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=589834 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=linux" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_env LANG #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=603159 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=589834 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=linux" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_env SHLVL #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=603159 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=589834 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=linux" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_env LANGUAGE #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=603159 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=589834 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=linux" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_env _ #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=328251 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=327965 perm=0755 } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_read /etc/selinux/config #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=12 major=0 minor=15 perm=0444 type=file } path1.parent={ uid=0 gid=0 ino=463 perm=0755 } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_read /selinux/mls #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=4026531844 major=0 minor=3 perm=0444 type=file } path1.parent={ uid=0 gid=0 ino=1 perm=0555 } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_read /proc/filesystems #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=605586 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=589842 perm=0755 } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_read /usr/lib/locale/locale-archive #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=329303 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=327681 perm=0755 } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_read /etc/nsswitch.conf #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=330197 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=327681 perm=0755 } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_read /etc/passwd #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=330196 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=327681 perm=0755 } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_read /etc/group #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=330196 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=327681 perm=0755 } <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id allow_read /etc/group |
You can compress these logs using "ccs-sortpolicy" command.
|
[root@tomoyo ~]# grep -A 3 -F 'profile=2 mode=permissive' /var/log/tomoyo/reject_log.conf | /usr/sbin/ccs-sortpolicy <kernel> /usr/sbin/httpd #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=603159 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=589834 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=linux" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } } allow_network TCP accept 0:0:0:0:0:ffff:c0a8:801 1507 <kernel> /usr/sbin/httpd /bin/sh #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=603159 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=589834 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=linux" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } } allow_execute /usr/bin/id <kernel> /usr/sbin/httpd /bin/sh /usr/bin/id #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=12 major=0 minor=15 perm=0444 type=file } path1.parent={ uid=0 gid=0 ino=463 perm=0755 } #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=328251 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=327965 perm=0755 } #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=329303 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=327681 perm=0755 } #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=330196 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=327681 perm=0755 } #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=330197 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=327681 perm=0755 } #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=4026531844 major=0 minor=3 perm=0444 type=file } path1.parent={ uid=0 gid=0 ino=1 perm=0555 } #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=603159 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=589834 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=linux" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } } #2010-01-12 16:11:32# profile=2 mode=permissive (global-pid=4641) task={ pid=4641 ppid=4637 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 state[0]=0 state[1]=0 state[2]=0 type!=execute_handler } path1={ uid=0 gid=0 ino=605586 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=589842 perm=0755 } allow_env LANG allow_env LANGUAGE allow_env PATH allow_env PWD allow_env SHLVL allow_env TERM allow_env _ allow_read /etc/group allow_read /etc/nsswitch.conf allow_read /etc/passwd allow_read /etc/selinux/config allow_read /proc/filesystems allow_read /selinux/mls allow_read /usr/lib/locale/locale-archive |
You can save the compressed logs into a temporary file. Then, you can edit as you need and append to currently used policy in the kernel using "ccs-loadpolicy". ccs-loadpolicy's "-" option means read from stdin, "d" option means domain_policy.conf .
|
[root@tomoyo ~]# grep -A 3 -F 'profile=2 mode=permissive' /var/log/tomoyo/reject_log.conf | /usr/sbin/ccs-sortpolicy > ~/rejected.log [root@tomoyo ~]# emacs ~/rejected.log [root@tomoyo ~]# /usr/sbin/ccs-loadpolicy -d < ~/rejected.log |
Since you are editing policy currently loaded into the kernel, changes will be lost if you shutdown the system without saving. Save exception_policy.conf and domain_poilicy.conf using "ccs-savepolicy" command.
| [root@tomoyo ~]# /usr/sbin/ccs-savepolicy a |
If your purpose of using TOMOYO Linux is for just analysis, this point is the goal of this procedure.
If your purpose of using TOMOYO Linux is for protection, proceed to next phase.