Chapter 6: How do I develop policy?
6.1. Patterning temporary files
A particular domain may require many different access permissions to many different resources. Since "Enforcing Mode" allows access to only resources explicitly defined, it is important to cover all necessary resources. To do this, permissions can be patterned. A patterned permission will allow multiple domain policy entries to be shortened into a single entry.
This is particularly important for temporary files due to the variety of single-use pathnames involved. They can either be handled in the manner described below, or handled interactively using the policy editor. For details on handling permissions interactively, see how to Converting ACL entries into patterns.
Use ccs-findtemp to find pathnames from domain policy that are potentially temporary files:
# /usr/sbin/ccs-findtemp < /proc/ccs/domain_policy
/tmp/RsACr8YD /tmp/RsXg3Aav /var/run/nscd/socket /var/spool/clientmqueue/dfoBPETPpH002933 /var/spool/clientmqueue/dfoBPETf92002944 /var/spool/clientmqueue/qfoBPETPpH002933 /var/spool/clientmqueue/qfoBPETf92002944 /var/spool/clientmqueue/xfoBPETPpH002933 /var/spool/clientmqueue/xfoBPETf92002944
In the example above, all except "/var/run/nscd/socket" can be considered to be temporary files. Thus, patterns can be made for these pathnames.
First, the type of pattern must be considered. The strings here appear to be random characters. Thus, the "\?" pattern which matches any single character other than "/", and the "\*" pattern which matches zero or more repetitions of any characters other than "/" can be used. See Wildcard expression rules for a list of possible wildcards.
Use ccs-patternize to convert into patterns non-interactively. Rewriting rules are specified in "/etc/ccs/tools/patternize.conf" file, as shown below:
# This file contains rewriting rules used by ccs-patternize command.
# Domain policy consists with domain declaration lines (which start with
# '<' ,) and acl declaration lines (which do not start with '<' ).
# You can refer the former using 'domain' keyword and the latter using 'acl'
# keyword.
#
# Words in each line are separated by a space character. Therefore, you can
# use 'domain[index]', 'acl[index]' for referring index'th word of the line.
# The index starts from 1, and 0 refers the whole line (i.e.
# 'domain[0]' = 'domain', 'acl[0]' = 'acl').
#
# Three operators are provided for conditional rewriting.
# '.contains' is for 'fgrep keyword' match.
# '.equals' is for 'grep ^keyword$' match.
# '.starts' is for 'grep ^keyword' match.
#
# Rewriting rules are defined using multi-lined chunks. A chunk is terminated
# by a 'rewrite' line which specifies old pattern and new pattern.
# A 'rewrite' line is evaluated only when all preceding 'domain' and 'acl'
# lines in that chunk have matched.
# Evaluation stops at first 'rewrite' line where a word matched old pattern.
# Therefore, no words are rewritten more than once.
#
# For user's convenience, new pattern can be omitted if old pattern is reused
# for new pattern.
# Please use TOMOYO Linux's escape rule (e.g. '\040' rather than '\ ' for
# representing a ' ' in a word).
# Files on proc filesystem.
rewrite path_pattern proc:/self/task/\$/fdinfo/\$
rewrite path_pattern proc:/self/task/\$/fd/\$
rewrite head_pattern proc:/self/task/\$/
rewrite path_pattern proc:/self/fdinfo/\$
rewrite path_pattern proc:/self/fd/\$
rewrite head_pattern proc:/self/
rewrite path_pattern proc:/\$/task/\$/fdinfo/\$
rewrite path_pattern proc:/\$/task/\$/fd/\$
rewrite head_pattern proc:/\$/task/\$/
rewrite path_pattern proc:/\$/fdinfo/\$
rewrite path_pattern proc:/\$/fd/\$
rewrite head_pattern proc:/\$/
# Files on devpts filesystem.
rewrite path_pattern devpts:/\$
# Files on pipe filesystem.
rewrite path_pattern pipe:[\$]
rewrite path_pattern pipefs:/[\$]
# Files on / partition.
rewrite tail_pattern /etc/mtab~\$
rewrite tail_pattern /etc/ccs/policy/\*/domain_policy.conf
rewrite tail_pattern /etc/ccs/policy/\*/exception_policy.conf
rewrite tail_pattern /etc/ccs/policy/\*/manager.conf
rewrite tail_pattern /etc/ccs/policy/\*/profile.conf
rewrite tail_pattern /etc/ccs/policy/\*/
# Files on /tmp/ partition.
rewrite tail_pattern /vte\?\?\?\?\?\?
rewrite tail_pattern /.ICE-unix/\$
rewrite tail_pattern /keyring-\?\?\?\?\?\?/socket.ssh
rewrite tail_pattern /orbit-\*/bonobo-activation-register-\X.lock
rewrite tail_pattern /orbit-\*/bonobo-activation-server-\X-ior
rewrite tail_pattern /orbit-\*/linc-\*
rewrite tail_pattern /orbit-\*/
rewrite tail_pattern /sh-thd-\$
rewrite tail_pattern /zman\?\?\?\?\?\?
# Files on home directory.
rewrite tail_pattern /.ICEauthority-\?
rewrite tail_pattern /.xauth\?\?\?\?\?\?
rewrite tail_pattern /.xauth\?\?\?\?\?\?-?
rewrite tail_pattern /.local/share/applications/preferred-mail-reader.desktop.\?\?\?\?\?\?
rewrite tail_pattern /.local/share/applications/preferred-web-browser.desktop.\?\?\?\?\?\?
# Files on /var/ partition.
rewrite tail_pattern /cache/fontconfig/\X-le64.cache-3
rewrite tail_pattern /lib/gdm/.pulse/\X-default-source
rewrite tail_pattern /lib/gdm/.pulse/\X-default-sink
rewrite tail_pattern /lib/gdm/.dbus/session-bus/\X-\X
rewrite tail_pattern /run/gdm/auth-for-\*/database-\?
rewrite tail_pattern /run/gdm/auth-for-\*/database
rewrite tail_pattern /run/gdm/auth-for-\*/
rewrite tail_pattern /spool/abrt/pyhook-\*/\{\*\}/\*
rewrite tail_pattern /spool/abrt/pyhook-\*/\{\*\}/
The "path_pattern" directive matches the whole pathname.
The "head_pattern" directive matches leading pathname.
The "tail_pattern" directive matches trailing pathname.
Append patterns for "/tmp/Rs\?\?\?\?\?\?" and "/var/spool/clientmqueue/\*" to /etc/ccs/tools/patternize.conf file:
rewrite tail_pattern /tmp/Rs\?\?\?\?\?\? rewrite tail_pattern /var/spool/clientmqueue/\*
Then, convert using ccs-patternize command and compare how it was changed using ccs-diffpolicy command:
# ccs-savepolicy -d > /tmp/old # ccs-patternize < /tmp/old > /tmp/new # ccs-diffpolicy /tmp/old /tmp/new
<kernel> /usr/sbin/httpd file write proc:/self/task/\$/attr/fscreate delete file write proc:/self/task/2766/attr/fscreate <kernel> /usr/sbin/httpd /bin/sh /bin/mail file create /tmp/Rs\?\?\?\?\?\? 0666 file read /tmp/Rs\?\?\?\?\?\? file unlink /tmp/Rs\?\?\?\?\?\? file write /tmp/Rs\?\?\?\?\?\? delete file create /tmp/RsACr8YD 0666 delete file create /tmp/RsXg3Aav 0666 delete file read /tmp/RsACr8YD delete file read /tmp/RsXg3Aav delete file unlink /tmp/RsACr8YD delete file unlink /tmp/RsXg3Aav delete file write /tmp/RsACr8YD delete file write /tmp/RsXg3Aav <kernel> /usr/sbin/httpd /bin/sh /bin/mail file ioctl pipefs:/[\$] 0x5413 delete file ioctl pipefs:/[11895] 0x5413 delete file ioctl pipefs:/[11965] 0x5413 <kernel> /usr/sbin/httpd /bin/sh /bin/mail /usr/sbin/sendmail file create /var/spool/clientmqueue/\* 0660 file read /var/spool/clientmqueue/\* file unlink /var/spool/clientmqueue/\* file write /var/spool/clientmqueue/\* delete file create /var/spool/clientmqueue/dfoBPETPpH002933 0660 delete file create /var/spool/clientmqueue/dfoBPETf92002944 0660 delete file create /var/spool/clientmqueue/qfoBPETPpH002933 0660 delete file create /var/spool/clientmqueue/qfoBPETf92002944 0660 delete file read /var/spool/clientmqueue/dfoBPETPpH002933 delete file read /var/spool/clientmqueue/dfoBPETf92002944 delete file unlink /var/spool/clientmqueue/dfoBPETPpH002933 delete file unlink /var/spool/clientmqueue/dfoBPETf92002944 delete file unlink /var/spool/clientmqueue/qfoBPETPpH002933 delete file unlink /var/spool/clientmqueue/qfoBPETf92002944 delete file unlink /var/spool/clientmqueue/xfoBPETPpH002933 delete file unlink /var/spool/clientmqueue/xfoBPETf92002944 delete file write /var/spool/clientmqueue/dfoBPETPpH002933 delete file write /var/spool/clientmqueue/dfoBPETf92002944 delete file write /var/spool/clientmqueue/qfoBPETPpH002933 delete file write /var/spool/clientmqueue/qfoBPETf92002944 <kernel> /usr/sbin/httpd /bin/sh /bin/ls file ioctl pipefs:/[\$] 0x5413 delete file ioctl pipefs:/[11965] 0x5413
In case the conversion did not achieve the desired result, "/tmp/new" can be edited with a text editor manually, or conversion can be retried after editing "/etc/ccs/tools/patternize.conf".
If the conversion has achieved the desired result, the changes can be applied to existing policy by loading the difference between the two:
# ccs-diffpolicy /tmp/old /tmp/new | /usr/sbin/ccs-loadpolicy -d
To convert only specific domains, the ccs-selectpolicy command can be used. For example, to update only "<kernel> /usr/sbin/httpd" and descendent domains, do the following:
# ccs-selectpolicy -r '<kernel> /usr/sbin/httpd' < /proc/ccs/domain_policy > /tmp/old-httpd # ccs-patternize < /tmp/old-httpd > /tmp/new-httpd # ccs-diffpolicy /tmp/old-httpd /tmp/new-httpd | ccs-loadpolicy -d
Conversion of a specific domain can also be managed by editing "/etc/ccs/tools/patternize.conf". The following line can be inserted before the "rewrite" line so that conversion is only done against "<kernel> /usr/sbin/httpd" and descendent domains:
domain.starts <kernel> /usr/sbin/httpd
6.2. Patterning file access permissions
Access permissions can be patterned to accommodate for files that are not necessarily accessed in "Learning Mode". For example, the domain policy can be changed to accommodate for web server contents:
|
Before |
After |
|---|---|
|
<kernel> /usr/sbin/httpd file read /var/www/html/index.html file read /var/www/html/alice/index.html file read /var/www/html/alice/page1.html file read /var/www/html/alice/page2.html file read /var/www/html/alice/image1.jpg file read /var/www/html/alice/image2.jpg file read /var/www/html/alice/archive/page1.html file read /var/www/html/alice/archive/image1.jpg file read /var/www/html/alice/archive/page2.html file read /var/www/html/alice/archive/image2.jpg file read /var/www/html/bob/index.html file read /var/www/html/bob/page1.html file read /var/www/html/bob/page2.html file read /var/www/html/bob/image1.jpg file read /var/www/html/bob/image2.jpg file read /var/www/html/bob/archive/page1.html file read /var/www/html/bob/archive/image1.jpg file read /var/www/html/bob/archive/page2.html file read /var/www/html/bob/archive/image2.jpg |
<kernel> /usr/sbin/httpd file read /var/www/html/\*.html file read /var/www/html/\{\*\}/\*.html file read /var/www/html/\{\*\}/\*.jpg |
Domain policy can be further simplified by placing directives in the exception policy, such as:
path_group WEB-CONTENTS /var/www/html/\*.html
path_group WEB-CONTENTS /var/www/html/\{\*\}/\*.html
path_group WEB-CONTENTS /var/www/html/\{\*\}/\*.jpg
The following can then be defined in domain policy:
<kernel> /usr/sbin/httpd file read @WEB-CONTENTS
The above conversion using ccs-editpolicy can also be managed using ccs-patternize. Add "path_group" to the exception policy like above (as ccs-patternize only deals with domain policy), and the following can then be added to "/etc/ccs/tools/patternize.conf" similar to section 6.1. Patterning temporary files:
domain.equals <kernel> /usr/sbin/httpd
acl.starts file read
rewrite path_pattern /var/www/html/\*.html @WEB-CONTENTS
domain.equals <kernel> /usr/sbin/httpd
acl.starts file read
rewrite path_pattern /var/www/html/\{\*\}/\*.html @WEB-CONTENTS
domain.equals <kernel> /usr/sbin/httpd
acl.starts file read
rewrite path_pattern /var/www/html/\{\*\}/\*.jpg @WEB-CONTENTS
6.3. Patterning numeric permissions
Patterns can be used for numeric parameters such as the creation mode of a file or a network's port numbers.
The following domain policy example permits the domain "<kernel> /usr/sbin/httpd" to accept connections from port numbers between 1024 and 65535:
|
Before |
After |
|---|---|
|
<kernel> /usr/sbin/httpd network inet stream accept 0:0:0:0:0:ffff:c0a8:801 3810 network inet stream accept 0:0:0:0:0:ffff:c0a8:801 3829 network inet stream accept 0:0:0:0:0:ffff:c0a8:801 3829 |
<kernel> /usr/sbin/httpd network inet stream accept 0:0:0:0:0:ffff:c0a8:801 1024-65535 |
Domain policy can be further simplified by placing directives in the exception policy, such as:
number_group WEB-CLIENT-PORTS 1024-65535
The following can then be defined in domain policy:
<kernel> /usr/sbin/httpd network inet stream accept 0:0:0:0:0:ffff:c0a8:801 @WEB-CLIENT-PORTS
The above conversion using ccs-editpolicy can also be managed using ccs-patternize. Add "number_group" to the exception policy like above, and the following can then be added to "/etc/ccs/tools/patternize.conf" similar to section 6.1. Patterning temporary files:
domain.equals <kernel> /usr/sbin/httpd acl.starts network inet stream accept rewrite number_pattern 1024-65535 @WEB-CLIENT-PORTS
6.4. Patterning network access permissions
Patterns can be made for IP addresses in domain policy, for example:
|
Before |
After |
|---|---|
|
<kernel> /usr/sbin/httpd network inet stream accept 0:0:0:0:0:0:0:1 @WEB-CLIENT-PORTS network inet stream accept 0:0:0:0:0:ffff:a00:1 @WEB-CLIENT-PORTS network inet stream accept 0:0:0:0:0:ffff:a00:a1 @WEB-CLIENT-PORTS network inet stream accept 10.0.0.10 @WEB-CLIENT-PORTS network inet stream accept 10.0.0.200 @WEB-CLIENT-PORTS |
<kernel> /usr/sbin/httpd network inet stream accept 0:0:0:0:0:0:0:1 @WEB-CLIENT-PORTS network inet stream accept 0:0:0:0:0:ffff:a00:1-0:0:0:0:0:ffff:a00:ff @WEB-CLIENT-PORTS network inet stream accept 10.0.0.1-10.0.0.255 @WEB-CLIENT-PORTS |
Domain policy can be further simplified by placing directives in the exception policy, such as:
address_group WEB-CLIENT-ADDRESS 0:0:0:0:0:0:0:1 address_group WEB-CLIENT-ADDRESS 0:0:0:0:0:ffff:a00:1-0:0:0:0:0:ffff:a00:ff address_group WEB-CLIENT-ADDRESS 10.0.0.1-10.0.0.255
The following can then be defined in domain policy:
<kernel> /usr/sbin/httpd network inet stream accept @WEB-CLIENT-ADDRESS @WEB-CLIENT-PORTS
The above conversion using ccs-editpolicy can also be managed using ccs-patternize. Add "address_group" to the exception policy like above, and the following can then be added to "/etc/ccs/tools/patternize.conf" similar to section 6.1. Patterning temporary files:
domain.equals <kernel> /usr/sbin/httpd acl.starts network inet stream accept rewrite address_pattern 0:0:0:0:0:0:0:1 @WEB-CLIENT-ADDRESS domain.equals <kernel> /usr/sbin/httpd acl.starts network inet stream accept rewrite address_pattern 0:0:0:0:0:ffff:a00:1-0:0:0:0:0:ffff:a00:ff @WEB-CLIENT-ADDRESS domain.equals <kernel> /usr/sbin/httpd acl.starts network inet stream accept rewrite address_pattern 10.0.0.1-10.0.0.255 @WEB-CLIENT-ADDRESS
6.5. Reviewing gathered permissions
Once you think you have done everything you want to allow Apache to do, run the policy editor and change the profile number to 2.
Note that Apache may have executed some external programs (e.g. /bin/sh, /usr/bin/perl, /usr/lib/sendmail) and thus has some descendent domains. Be sure to change the profile number for all descendent domains as well.
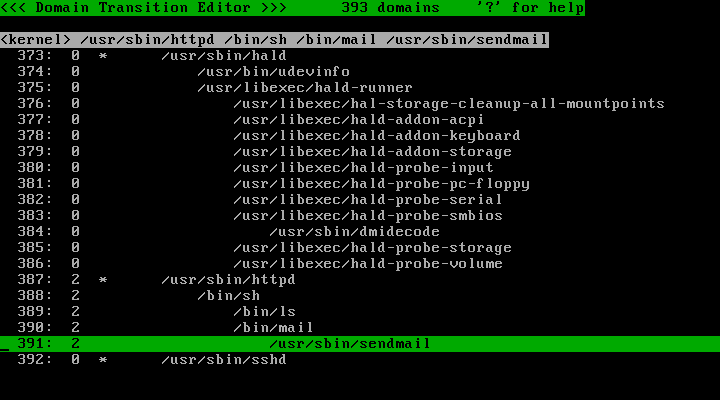
Quit the policy editor and continue using Apache:
You can check the /proc/ccs/stat interface for how many times policy violations have occurred and the last time a policy violation occurred:
# cat /proc/ccs/stat
Policy update: 1571 (Last: 2010/12/25 16:10:48) Policy violation in learning mode: 453 (Last: 2010/12/25 15:33:21) Policy violation in permissive mode: 22 (Last: 2010/12/25 15:47:10) Policy violation in enforcing mode: 0 Memory used by policy: 165728 Memory used by audit log: 0 (Quota: 16777216) Memory used by query message: 0 (Quota: 1048576) Total memory used: 165728
6.6. Using audit logs to develop policy (optional)
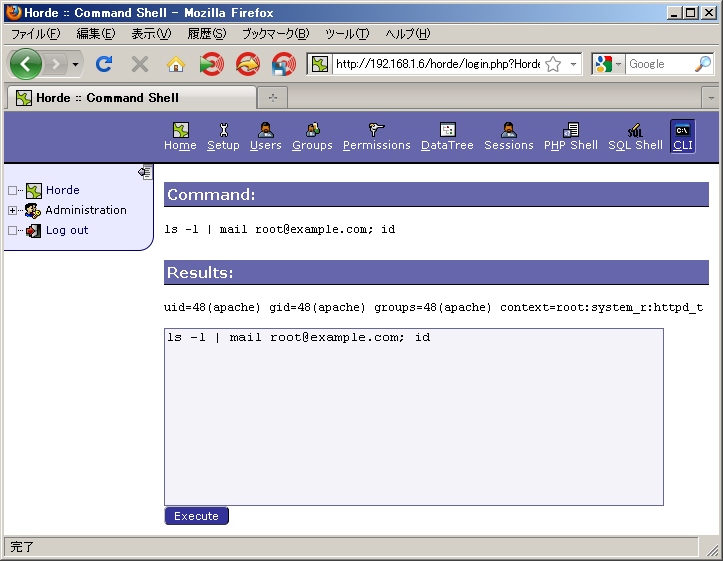
If audit logs have been configured at 4.6. Saving audit logs (optional), necessary permissions can be picked up from "/var/log/tomoyo/reject_002.log":
# cat /var/log/tomoyo/reject_002.log
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1545499 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=1540116 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=vt100" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } }
<kernel> /usr/sbin/httpd /bin/sh
file execute /usr/bin/id
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
use_profile 2
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
use_group 0
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1545499 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=1540116 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=vt100" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
misc env TERM
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1545499 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=1540116 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=vt100" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
misc env PATH
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1545499 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=1540116 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=vt100" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
misc env PWD
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1545499 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=1540116 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=vt100" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
misc env LANG
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1545499 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=1540116 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=vt100" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
misc env SHLVL
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1545499 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=1540116 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=vt100" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
misc env LANGUAGE
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1545499 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=1540116 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=vt100" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
misc env _
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1245682 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=1245419 perm=0755 }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
file read /etc/selinux/config
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=12 major=0 minor=15 perm=0444 type=file } path1.parent={ uid=0 gid=0 ino=496 perm=0755 }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
file read selinuxfs:/mls
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
network unix stream connect /var/run/setrans/.setrans-unix
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=4026531844 major=0 minor=3 perm=0444 type=file } path1.parent={ uid=0 gid=0 ino=1 perm=0555 }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
file read proc:/filesystems
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1547485 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=1540124 perm=0755 }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
file read /usr/lib/locale/locale-archive
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
network unix stream connect /var/run/setrans/.setrans-unix
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
network unix stream connect /var/run/nscd/socket
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
network unix stream connect /var/run/nscd/socket
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1245231 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=1245185 perm=0755 }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
file read /etc/nsswitch.conf
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1245924 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=1245185 perm=0755 }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
file read /etc/passwd
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
network unix stream connect /var/run/nscd/socket
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
network unix stream connect /var/run/nscd/socket
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1245902 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=1245185 perm=0755 }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
file read /etc/group
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1245902 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=1245185 perm=0755 }
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
file read /etc/group
These can be compressed with the "ccs-sortpolicy" command:
# cat /var/log/tomoyo/reject_002.log | /usr/sbin/ccs-sortpolicy
<kernel> /usr/sbin/httpd /bin/sh
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler }
file execute /usr/bin/id
<kernel> /usr/sbin/httpd /bin/sh /usr/bin/id
use_profile 2
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler }
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=12 major=0 minor=15 perm=0444 type=file } path1.parent={ uid=0 gid=0 ino=496 perm=0755 }
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1245231 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=1245185 perm=0755 }
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1245682 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=1245419 perm=0755 }
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1245902 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=1245185 perm=0755 }
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1245924 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=1245185 perm=0755 }
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1545499 major=8 minor=1 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=1540116 perm=0755 } exec={ realpath="/usr/bin/id" argc=1 envc=7 argv[]={ "id" } envp[]={ "TERM=vt100" "PATH=/sbin:/usr/sbin:/bin:/usr/bin" "PWD=/usr/share/horde/admin" "LANG=en_US.UTF-8" "SHLVL=3" "LANGUAGE=en_US.UTF-8" "_=/usr/bin/id" } }
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=1547485 major=8 minor=1 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=1540124 perm=0755 }
#2010/12/25 15:47:10# profile=2 mode=permissive granted=no (global-pid=3390) task={ pid=3390 ppid=3386 uid=48 gid=48 euid=48 egid=48 suid=48 sgid=48 fsuid=48 fsgid=48 type!=execute_handler } path1={ uid=0 gid=0 ino=4026531844 major=0 minor=3 perm=0444 type=file } path1.parent={ uid=0 gid=0 ino=1 perm=0555 }
file read /etc/group
file read /etc/nsswitch.conf
file read /etc/passwd
file read /etc/selinux/config
file read /usr/lib/locale/locale-archive
file read proc:/filesystems
file read selinuxfs:/mls
misc env LANG
misc env LANGUAGE
misc env PATH
misc env PWD
misc env SHLVL
misc env TERM
misc env _
network unix stream connect /var/run/nscd/socket
network unix stream connect /var/run/setrans/.setrans-unix
use_group 0
These compressed logs can be saved into a temporary file. These can then be edited as required and appended to current policy using the ccs-loadpolicy command:
# cat /var/log/tomoyo/reject_002.log | /usr/sbin/ccs-sortpolicy > ~/rejected.log # vim ~/rejected.log # /usr/sbin/ccs-loadpolicy -d < ~/rejected.log
Since you are editing policy currently loaded into the kernel, changes will be lost if you shutdown the system without saving. Save "exception_policy.conf", "domain_policy.conf", "profile.conf" and "manager.conf" using this command:
# /usr/sbin/ccs-savepolicy