TOMOYO Linux LiveCD Tutorial for Ubuntu 12.04
- About this page
- Getting LiveCD
- Booting from LiveCD
- Using LiveCD
- Restricting accesses
- (appendix) Installing Ubuntu + TOMOYO on your hard drive
- For more information
About this page
This document explains how to use the TOMOYO Linux LiveCD. The CD image contains Ubuntu with a TOMOYO Linux kernel and userspace tools pre-installed. You can use this CD to try TOMOYO Linux without any effects to the existing system.
Getting LiveCD
You can download ISO image file of TOMOYO Linux LiveCD at Download page.
Please burn the ISO image into CD-R. You can use VMware Player if you don't want to burn the ISO image.
Booting from LiveCD
When you boot your PC from LiveCD, you will see the following screen.
By scrolling the language selection bar, you can choose language you want to use.
By choosing "Try Ubuntu", you will see the following screen. This LiveCD is almost the same with normal Ubuntu LiveCD, except that several icons are added by TOMOYO Linux.
Using LiveCD
Please double-click the icon named "TOMOYO Linux Policy Violation Log". Then you can see the following window:
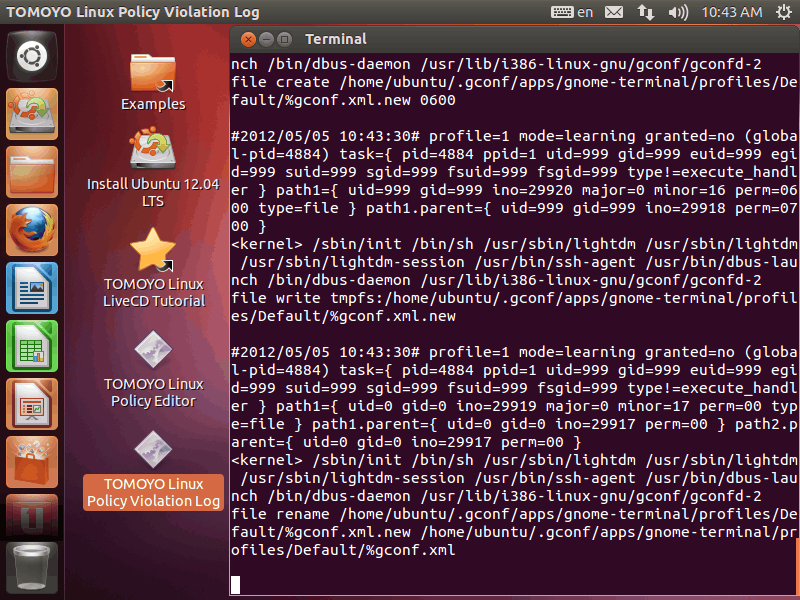
This window is showing accesses which violate the policy of TOMOYO Linux. New violation accesses are showed instantly. Since this LiveCD is configured to boot without predefined policy, all accesses are recorded to policy violation logs. Please keep the window shown and operate some functions. The logs that what process accesses which resources are shown in real time.
Then, please double-click the icon named "TOMOYO Linux Policy Editor". Then the following window is shown:
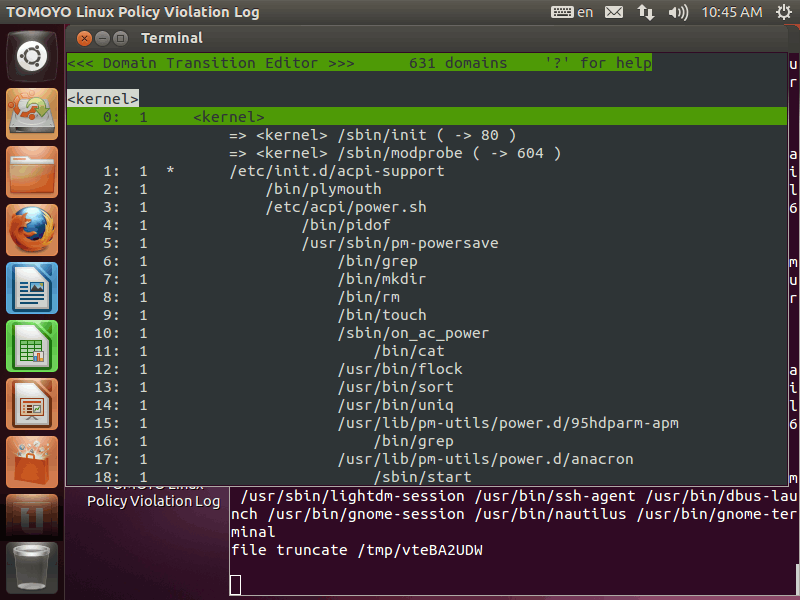
This window displays all invoked processes in the tree structure. Each line is called "domain". All invoked processes from the beginning of boot sequence are monitored by TOMOYO Linux kernel. The information that what process accesses which resources is recorded as a TOMOYO Linux policy. You can understand your Linux's behavior easily by browsing TOMOYO Linux policy. That's the greatest characteristic of TOMOYO Linux.
The first situation of policy editor shows process invocation history whose origin is <kernel>. Please scroll down as you like and confirm the process invoked in your system.
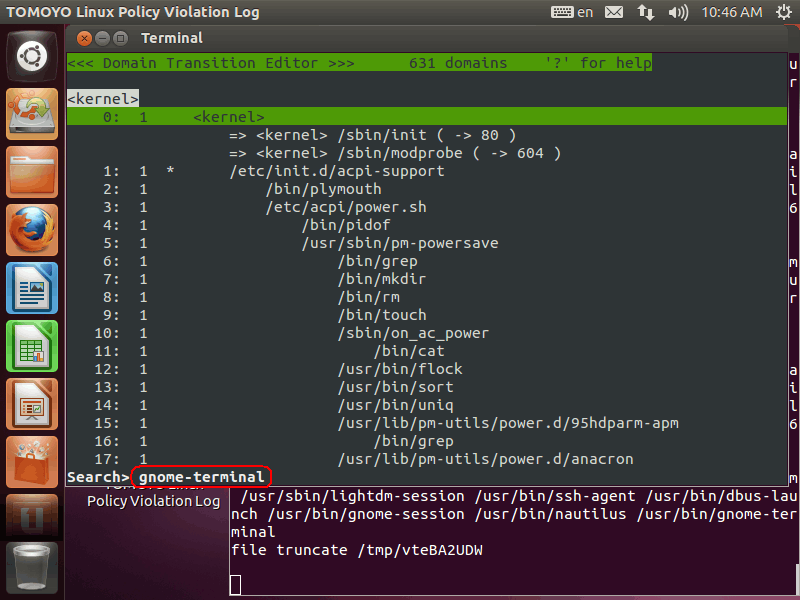
Let's try to find the process named "gnome-terminal". Please press 'F' key, then a prompt is shown in the bottom of the window. Please input "gnome-terminal" and press 'Enter' key:
You can see that gnome-terminal invoked /usr/sbin/sudo, and /usr/sbin/sudo invoked /usr/bin/tail and /usr/sbin/ccs-editpolicy :
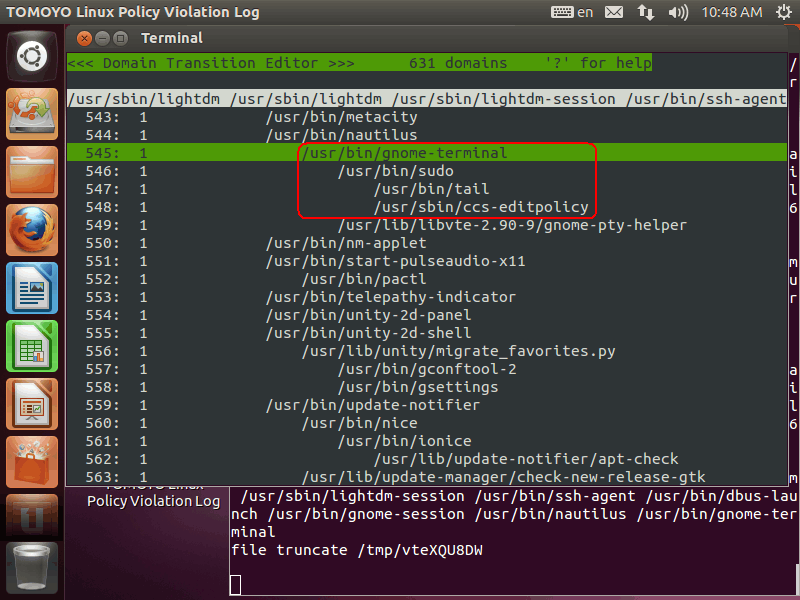
Please press 'Enter' key on /usr/bin/tail :
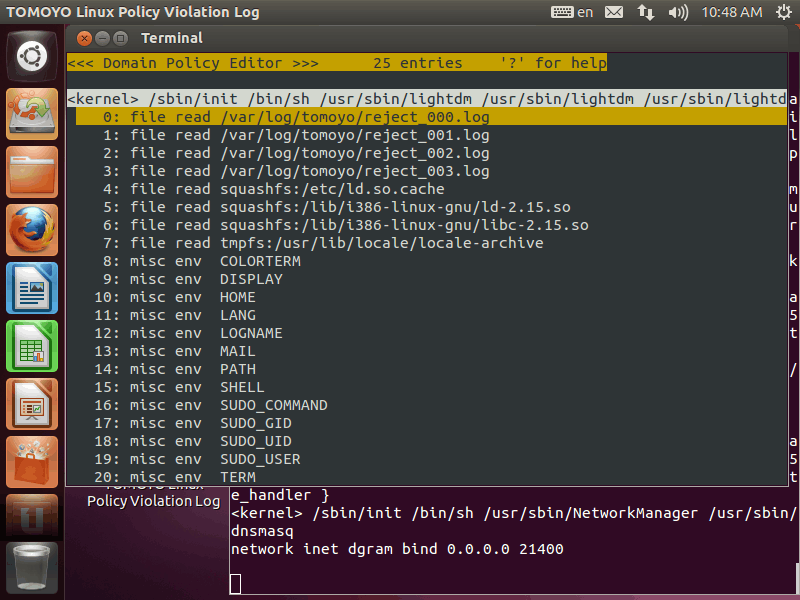
The leftmost number of each line is line number, and next word is the access permission. "file execute" means execute, "file write" means open for writing, "file read" means open for reading, "misc env" means accepting this environment variable name. These lines show the tail command read a locale file and /var/log/tomoyo/reject_000.log /var/log/tomoyo/reject_001.log /var/log/tomoyo/reject_002.log /var/log/tomoyo/reject_003.log . This policy is the result of learning the behavior of double-clicking "TOMOYO Linux Policy Violation Log" icon.
Please press 'Enter' key to go back to the previous domain-tree view. Please browse several domains and permissions as you like.
Restricting accesses
Now let's try to restrict accesses by TOMOYO Linux. Please keep the policy editor in background, and click "Dash home" icon and then click "Terminal" icon which appears by typing "terminal" into the search bar:
After starting terminal, please go back to the policy editor and press 'R' key to reload TOMOYO Linux policy. Please find /bin/bash that is the child of gnome-terminal . To find bash, you can use 'F' key like the previous operations. To find next match, you can use 'N' key:
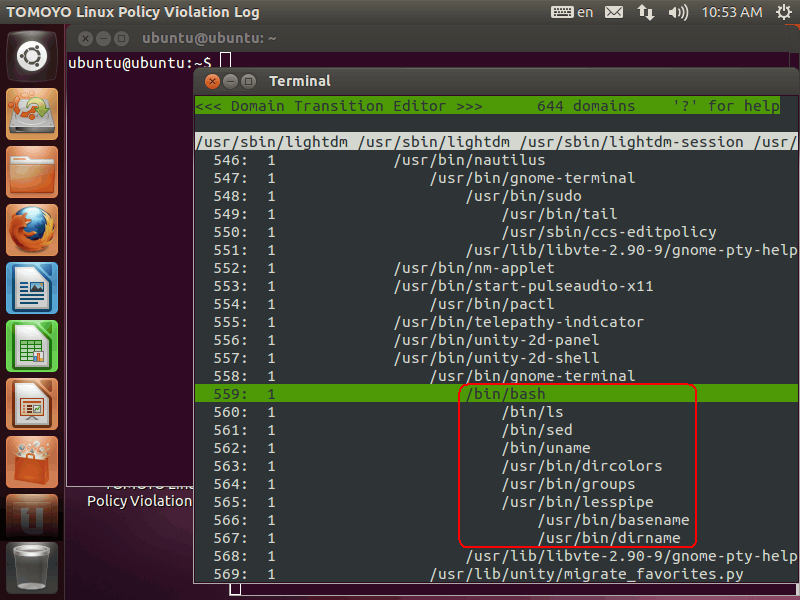
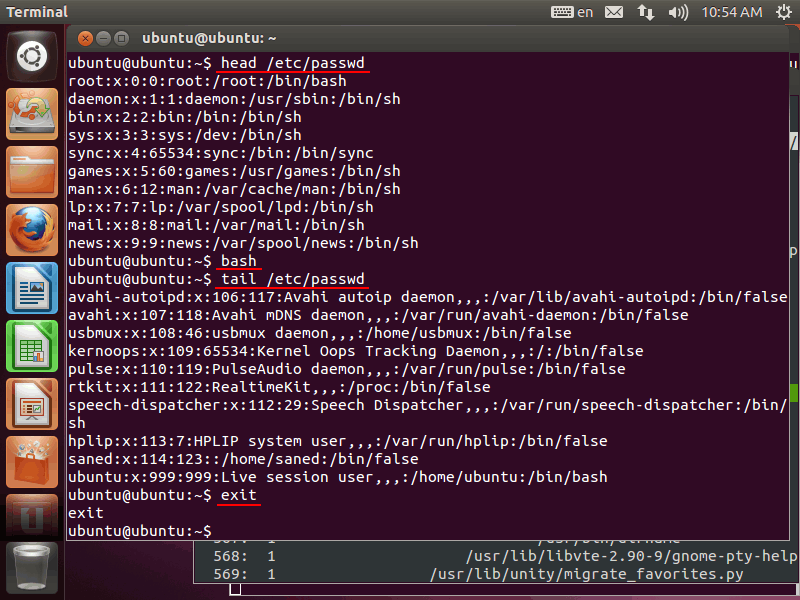
This bash is running in the "Terminal" window. There are domains of ls, sed, and so on, which were automatically executed in bash start sequence. Please type the following command in the terminal:
$ head /etc/passwd $ bash $ tail /etc/passwd $ exit
Then, please go back the policy editor and press 'R' key, and you can see that domains of executed programs are appended:
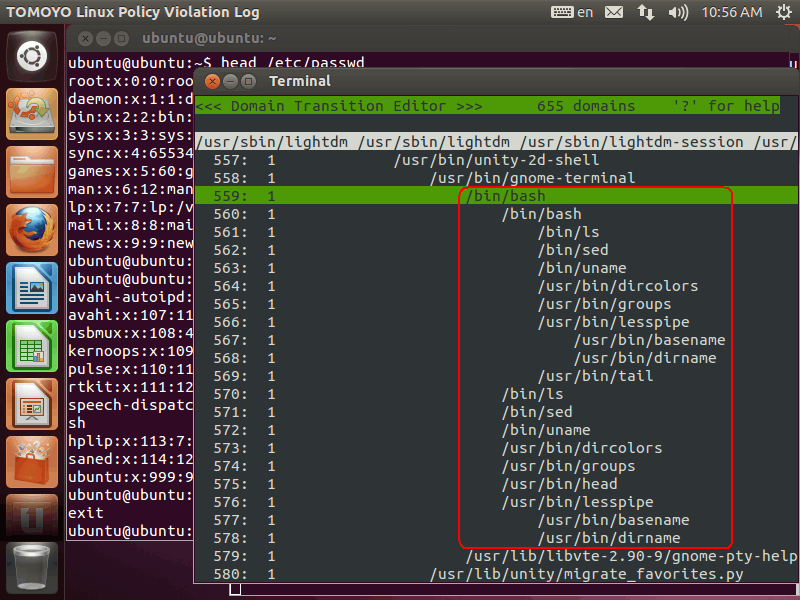
Please pay attention to the numbers in the next of line numbers. All lines are currently '1':
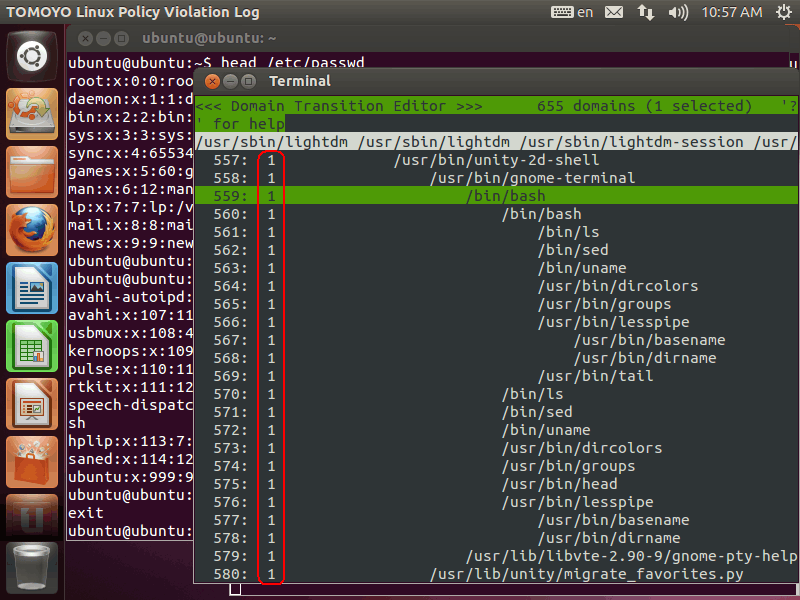
These numbers show the process's running mode of TOMOYO Linux, which is called profile number. The profile numbers of are 0-3 and all domains in this LiveCD are initially assigned profile number 1 (learning mode):
| profile number | meanings |
|---|---|
| 0 | disabled mode (TOMOYO Linux do nothing) |
| 1 | leaning mode (access requests that violated policy are accepted and policy is updated to allow such access requests) |
| 2 | permissive mode (access requests that violated policy are accepted) |
| 3 | enforcing mode (access requests that violated policy are debied) |
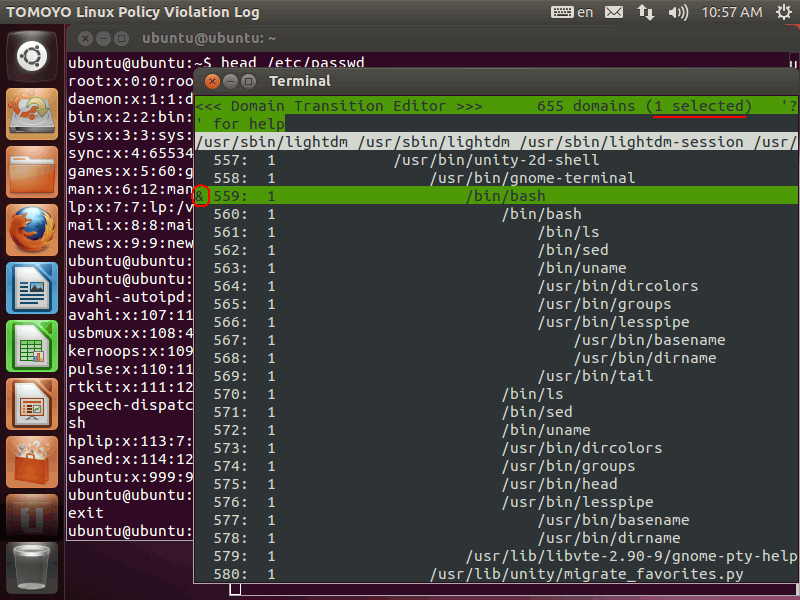
To enable TOMOYO Linux access restriction, you need to assign profile number 3 to domain. Let's restrict operations using bash invoked from gnome-terminal. Please press Space key at bash just below gnome-terminal, and you will see '&' mark appeared at the left of the line number. This '&' is the 'selected' mark:
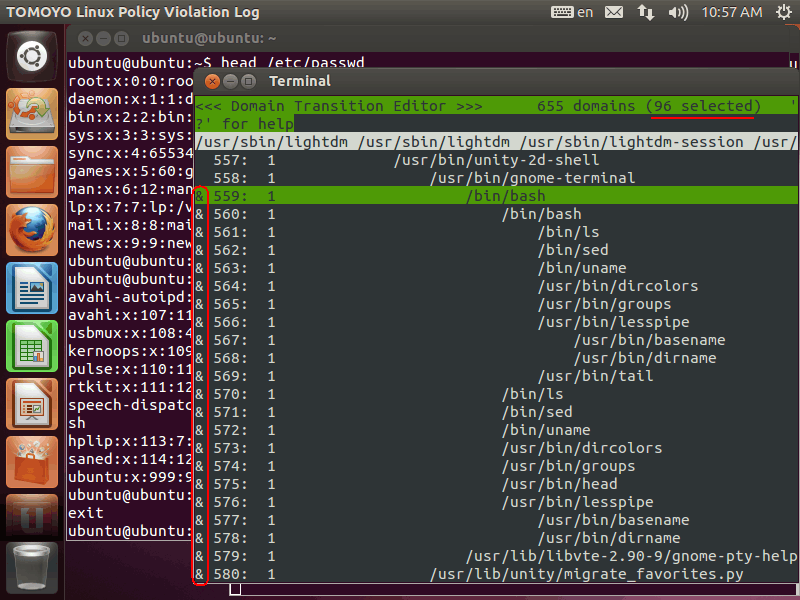
Then, please press 'C' key, and you will get '&' mark copied to all lines below:
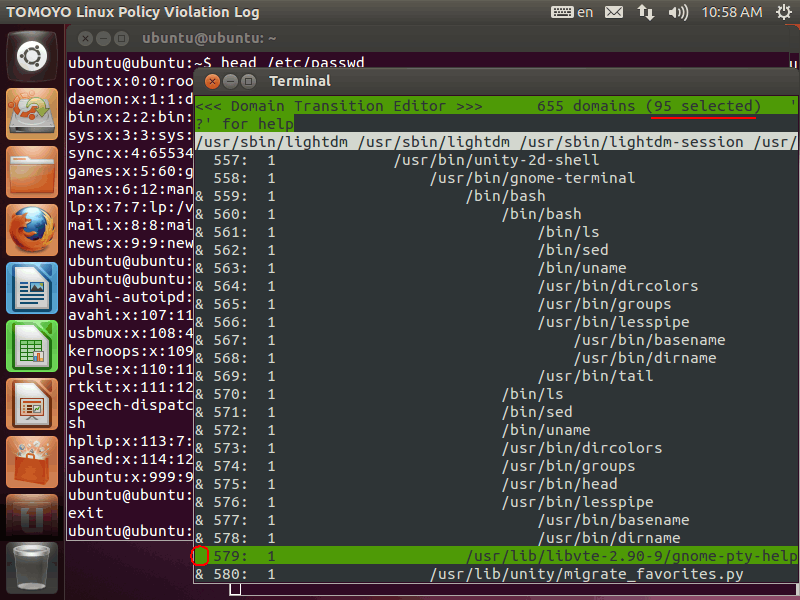
Then, please press Space key at gnome-pty-helper, and you will see '&' mark disappeared:
Then, please press 'C' key, and you will get '&' mark cleared from all lines below:
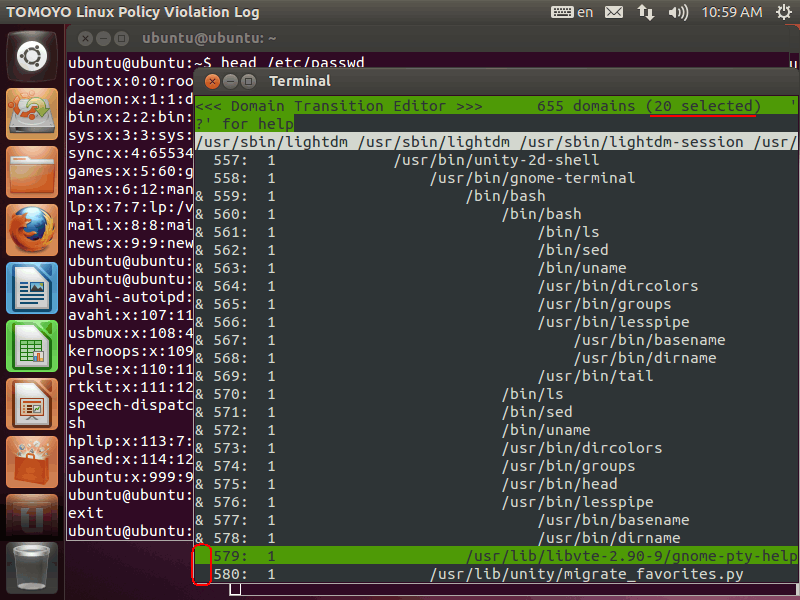
Then, please press 'S' key then prompt is shown in the bottom of the window. Please input "3" and press 'Enter' key:
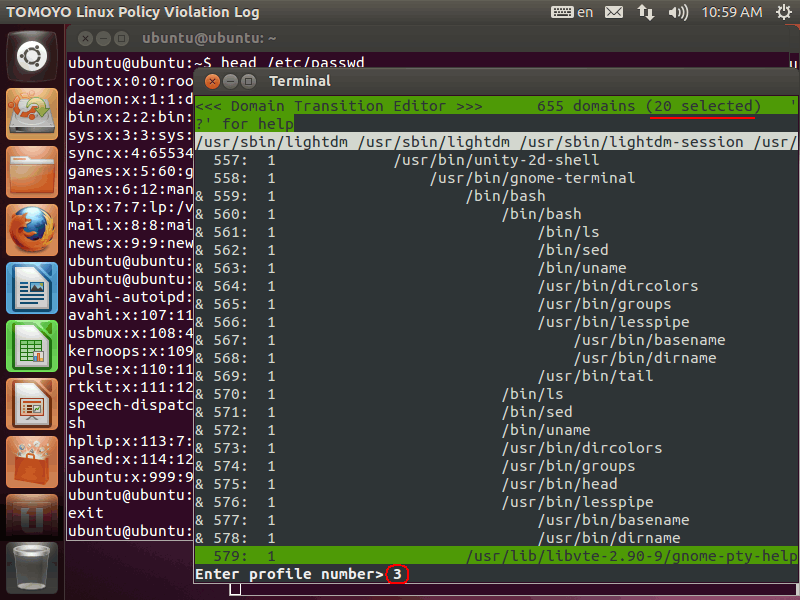
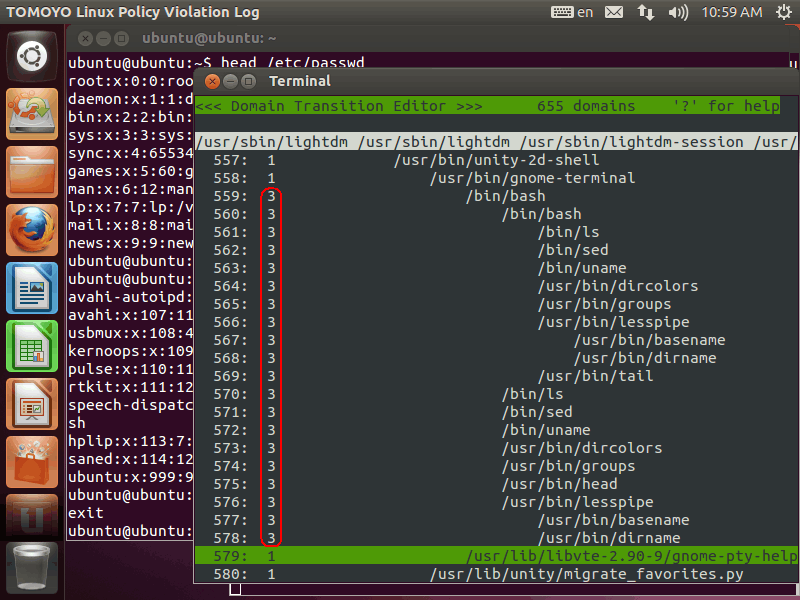
Profile number 3 is assigned to the selected domains:
bash invoked from gnome-terminal is already running in enforcing mode. Please execute some commands in the terminal. Commands that are not executed in learning mode will be denied. In the following window, "head /etc/password" is granted, but executions of "ps" and "id" are denied:
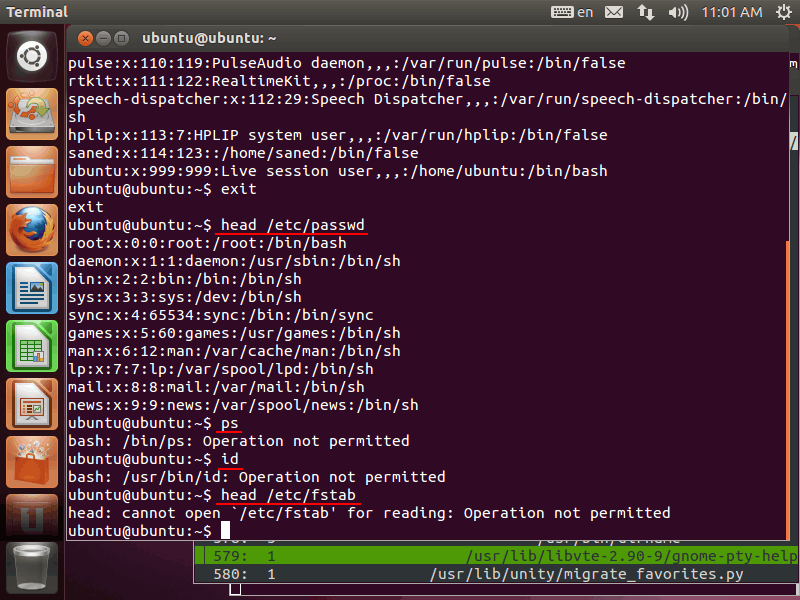
In addition, first-level bash can't execute "tail /etc/passwd", but second-level bash can do it:
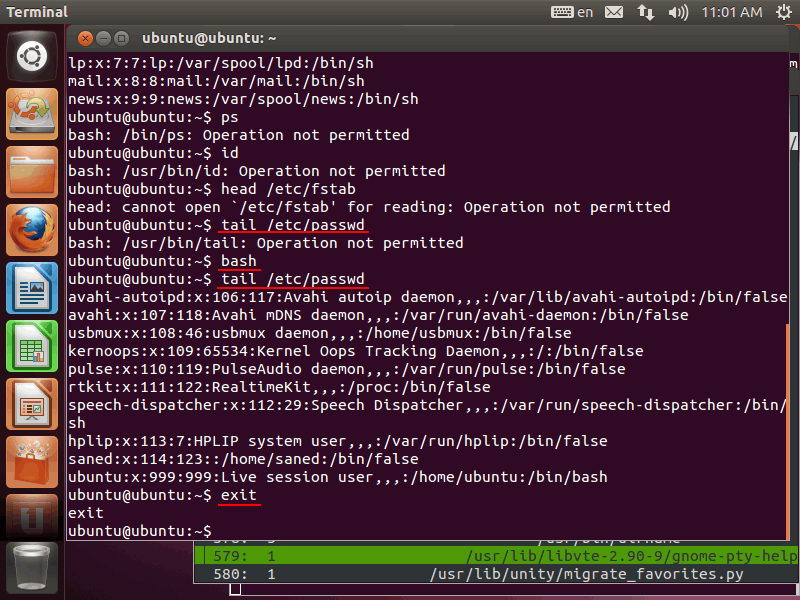
This is because TOMOYO Linux distinguishes processes according to their invocation history. In current policy, the following two bashes exist.
- bash executed by gnome-terminal
- bash executed by bash executed by gnome-terminal
head command is only permitted in the first bash, and tail command is only permitted in the second bash. TOMOYO Linux monitors all processes from system boot sequence, and processes are distinguished by fine-grained method.
You can find below entries which contains "mode=enforcing" line from /var/log/tomoyo/reject_003.log . Not only requested pathnames but also process credential information / command line arguments / environment variables etc. are recorded. If you want to restrict access more strictly, you can utilize these variables as needed.
#2012/05/05 11:00:30# profile=3 mode=enforcing granted=no (global-pid=5555) task={ pid=5555 ppid=5423 uid=999 gid=999 euid=999 egid=999 suid=999 sgid=999 fsuid=999 fsgid=999 type!=execute_handler } path1={ uid=0 gid=0 ino=32204 major=7 minor=0 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=1525 perm=0755 } exec={ realpath="squashfs:/bin/ps" argc=1 envc=36 argv[]={ "ps" } envp[]={ "SSH_AGENT_PID=4837" "GPG_AGENT_INFO=/tmp/keyring-XyKrEp/gpg:0:1" "TERM=xterm" "SHELL=/bin/bash" "XDG_SESSION_COOKIE=d20f16b3e9fc48f3d4e425ef00000017-1336091640.53174-1297177047" "WINDOWID=58720261" "GNOME_KEYRING_CONTROL=/tmp/keyring-XyKrEp" "USER=ubuntu" "LS_COLORS=rs=0:di=01;34:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:su=37;41:sg=30;43:ca=30;41:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.arj=01;31:*.taz=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.zip=01;31:*.z=01;31:*.Z=01;31:*.dz=01;31:*.gz=01;31:*.lz=01;31:*.xz=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=01;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.jpg=01;35:*.jpeg=01;35:*.gif=01;35:*.bmp=01;35:*.pbm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01;35:*.mkv=01;35:*.webm=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.flv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.axv=01;35:*.anx=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.mid=00;36:*.midi=00;36:*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.axa=00;36:*.oga=00;36:*.spx=00;36:*.xspf=00;36:" "XDG_SESSION_PATH=/org/freedesktop/DisplayManager/Session0" "XDG_SEAT_PATH=/org/freedesktop/DisplayManager/Seat0" "SSH_AUTH_SOCK=/tmp/keyring-XyKrEp/ssh" "SESSION_MANAGER=local/ubuntu:@/tmp/.ICE-unix/4799,unix/ubuntu:/tmp/.ICE-unix/4799" "DEFAULTS_PATH=/usr/share/gconf/ubuntu-2d.default.path" "XDG_CONFIG_DIRS=/etc/xdg/xdg-ubuntu-2d:/etc/xdg" "PATH=/usr/lib/lightdm/lightdm:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games" "DESKTOP_SESSION=ubuntu-2d" "PWD=/home/ubuntu" "LANG=en_US.UTF-8" "MANDATORY_PATH=/usr/share/gconf/ubuntu-2d.mandatory.path" "UBUNTU_MENUPROXY=libappmenu.so" "GDMSESSION=ubuntu-2d" "SHLVL=1" "HOME=/home/ubuntu" "GNOME_DESKTOP_SESSION_ID=this-is-deprecated" "LOGNAME=ubuntu" "XDG_DATA_DIRS=/usr/share/ubuntu-2d:/usr/share/gnome:/usr/local/share/:/usr/share/" "DBUS_SESSION_BUS_ADDRESS=unix:abstract=/tmp/dbus-1zeCZoSrS5,guid=10a6e1e3136d655ec8ff22a000000234" "LESSOPEN=|\040/usr/bin/lesspipe\040%s" "DISPLAY=:0" "XDG_CURRENT_DESKTOP=Unity" "LESSCLOSE=/usr/bin/lesspipe\040%s\040%s" "RUNNING_UNDER_GDM=yes" "COLORTERM=gnome-terminal" "XAUTHORITY=/home/ubuntu/.Xauthority" "_=/bin/ps" } }
<kernel> /sbin/init /bin/sh /usr/sbin/lightdm /usr/sbin/lightdm /usr/sbin/lightdm-session /usr/bin/ssh-agent /usr/bin/dbus-launch /usr/bin/gnome-session /usr/bin/unity-2d-shell /usr/bin/gnome-terminal /bin/bash
file execute /bin/ps
#2012/05/05 11:00:30# profile=3 mode=enforcing granted=no (global-pid=5555) task={ pid=5555 ppid=5423 uid=999 gid=999 euid=999 egid=999 suid=999 sgid=999 fsuid=999 fsgid=999 type!=execute_handler } path1={ uid=0 gid=0 ino=32204 major=7 minor=0 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=1525 perm=0755 }
<kernel> /sbin/init /bin/sh /usr/sbin/lightdm /usr/sbin/lightdm /usr/sbin/lightdm-session /usr/bin/ssh-agent /usr/bin/dbus-launch /usr/bin/gnome-session /usr/bin/unity-2d-shell /usr/bin/gnome-terminal /bin/bash
file read squashfs:/bin/ps
#2012/05/05 11:00:43# profile=3 mode=enforcing granted=no (global-pid=5556) task={ pid=5556 ppid=5423 uid=999 gid=999 euid=999 egid=999 suid=999 sgid=999 fsuid=999 fsgid=999 type!=execute_handler } path1={ uid=0 gid=0 ino=180922 major=7 minor=0 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=17658 perm=0755 } exec={ realpath="squashfs:/usr/bin/id" argc=1 envc=36 argv[]={ "id" } envp[]={ "SSH_AGENT_PID=4837" "GPG_AGENT_INFO=/tmp/keyring-XyKrEp/gpg:0:1" "TERM=xterm" "SHELL=/bin/bash" "XDG_SESSION_COOKIE=d20f16b3e9fc48f3d4e425ef00000017-1336091640.53174-1297177047" "WINDOWID=58720261" "GNOME_KEYRING_CONTROL=/tmp/keyring-XyKrEp" "USER=ubuntu" "LS_COLORS=rs=0:di=01;34:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:su=37;41:sg=30;43:ca=30;41:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.arj=01;31:*.taz=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.zip=01;31:*.z=01;31:*.Z=01;31:*.dz=01;31:*.gz=01;31:*.lz=01;31:*.xz=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=01;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.jpg=01;35:*.jpeg=01;35:*.gif=01;35:*.bmp=01;35:*.pbm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01;35:*.mkv=01;35:*.webm=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.flv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.axv=01;35:*.anx=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.mid=00;36:*.midi=00;36:*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.axa=00;36:*.oga=00;36:*.spx=00;36:*.xspf=00;36:" "XDG_SESSION_PATH=/org/freedesktop/DisplayManager/Session0" "XDG_SEAT_PATH=/org/freedesktop/DisplayManager/Seat0" "SSH_AUTH_SOCK=/tmp/keyring-XyKrEp/ssh" "SESSION_MANAGER=local/ubuntu:@/tmp/.ICE-unix/4799,unix/ubuntu:/tmp/.ICE-unix/4799" "DEFAULTS_PATH=/usr/share/gconf/ubuntu-2d.default.path" "XDG_CONFIG_DIRS=/etc/xdg/xdg-ubuntu-2d:/etc/xdg" "PATH=/usr/lib/lightdm/lightdm:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games" "DESKTOP_SESSION=ubuntu-2d" "PWD=/home/ubuntu" "LANG=en_US.UTF-8" "MANDATORY_PATH=/usr/share/gconf/ubuntu-2d.mandatory.path" "UBUNTU_MENUPROXY=libappmenu.so" "GDMSESSION=ubuntu-2d" "SHLVL=1" "HOME=/home/ubuntu" "GNOME_DESKTOP_SESSION_ID=this-is-deprecated" "LOGNAME=ubuntu" "XDG_DATA_DIRS=/usr/share/ubuntu-2d:/usr/share/gnome:/usr/local/share/:/usr/share/" "DBUS_SESSION_BUS_ADDRESS=unix:abstract=/tmp/dbus-1zeCZoSrS5,guid=10a6e1e3136d655ec8ff22a000000234" "LESSOPEN=|\040/usr/bin/lesspipe\040%s" "DISPLAY=:0" "XDG_CURRENT_DESKTOP=Unity" "LESSCLOSE=/usr/bin/lesspipe\040%s\040%s" "RUNNING_UNDER_GDM=yes" "COLORTERM=gnome-terminal" "XAUTHORITY=/home/ubuntu/.Xauthority" "_=/usr/bin/id" } }
<kernel> /sbin/init /bin/sh /usr/sbin/lightdm /usr/sbin/lightdm /usr/sbin/lightdm-session /usr/bin/ssh-agent /usr/bin/dbus-launch /usr/bin/gnome-session /usr/bin/unity-2d-shell /usr/bin/gnome-terminal /bin/bash
file execute /usr/bin/id
#2012/05/05 11:00:43# profile=3 mode=enforcing granted=no (global-pid=5556) task={ pid=5556 ppid=5423 uid=999 gid=999 euid=999 egid=999 suid=999 sgid=999 fsuid=999 fsgid=999 type!=execute_handler } path1={ uid=0 gid=0 ino=180922 major=7 minor=0 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=17658 perm=0755 }
<kernel> /sbin/init /bin/sh /usr/sbin/lightdm /usr/sbin/lightdm /usr/sbin/lightdm-session /usr/bin/ssh-agent /usr/bin/dbus-launch /usr/bin/gnome-session /usr/bin/unity-2d-shell /usr/bin/gnome-terminal /bin/bash
file read squashfs:/usr/bin/id
#2012/05/05 11:00:54# profile=3 mode=enforcing granted=no (global-pid=5557) task={ pid=5557 ppid=5423 uid=999 gid=999 euid=999 egid=999 suid=999 sgid=999 fsuid=999 fsgid=999 type!=execute_handler } path1={ uid=0 gid=0 ino=7922 major=0 minor=16 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=7921 perm=0755 }
<kernel> /sbin/init /bin/sh /usr/sbin/lightdm /usr/sbin/lightdm /usr/sbin/lightdm-session /usr/bin/ssh-agent /usr/bin/dbus-launch /usr/bin/gnome-session /usr/bin/unity-2d-shell /usr/bin/gnome-terminal /bin/bash /usr/bin/head
file read tmpfs:/etc/fstab
#2012/05/05 11:00:54# profile=3 mode=enforcing granted=no (global-pid=5557) task={ pid=5557 ppid=5423 uid=999 gid=999 euid=999 egid=999 suid=999 sgid=999 fsuid=999 fsgid=999 type!=execute_handler } path1={ uid=0 gid=0 ino=31669 major=7 minor=0 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=1516 perm=0755 }
<kernel> /sbin/init /bin/sh /usr/sbin/lightdm /usr/sbin/lightdm /usr/sbin/lightdm-session /usr/bin/ssh-agent /usr/bin/dbus-launch /usr/bin/gnome-session /usr/bin/unity-2d-shell /usr/bin/gnome-terminal /bin/bash /usr/bin/head
file read squashfs:/etc/locale.alias
#2012/05/05 11:00:54# profile=3 mode=enforcing granted=no (global-pid=5557) task={ pid=5557 ppid=5423 uid=999 gid=999 euid=999 egid=999 suid=999 sgid=999 fsuid=999 fsgid=999 type!=execute_handler } path1={ uid=0 gid=0 ino=169902 major=7 minor=0 perm=0644 type=file } path1.parent={ uid=0 gid=0 ino=16901 perm=0755 }
<kernel> /sbin/init /bin/sh /usr/sbin/lightdm /usr/sbin/lightdm /usr/sbin/lightdm-session /usr/bin/ssh-agent /usr/bin/dbus-launch /usr/bin/gnome-session /usr/bin/unity-2d-shell /usr/bin/gnome-terminal /bin/bash /usr/bin/head
file read squashfs:/usr/share/locale-langpack/en/LC_MESSAGES/coreutils.mo
#2012/05/05 11:01:27# profile=3 mode=enforcing granted=no (global-pid=5559) task={ pid=5559 ppid=5423 uid=999 gid=999 euid=999 egid=999 suid=999 sgid=999 fsuid=999 fsgid=999 type!=execute_handler } path1={ uid=0 gid=0 ino=181657 major=7 minor=0 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=17658 perm=0755 } exec={ realpath="squashfs:/usr/bin/tail" argc=2 envc=36 argv[]={ "tail" "/etc/passwd" } envp[]={ "SSH_AGENT_PID=4837" "GPG_AGENT_INFO=/tmp/keyring-XyKrEp/gpg:0:1" "TERM=xterm" "SHELL=/bin/bash" "XDG_SESSION_COOKIE=d20f16b3e9fc48f3d4e425ef00000017-1336091640.53174-1297177047" "WINDOWID=58720261" "GNOME_KEYRING_CONTROL=/tmp/keyring-XyKrEp" "USER=ubuntu" "LS_COLORS=rs=0:di=01;34:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:su=37;41:sg=30;43:ca=30;41:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.arj=01;31:*.taz=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.zip=01;31:*.z=01;31:*.Z=01;31:*.dz=01;31:*.gz=01;31:*.lz=01;31:*.xz=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=01;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.jpg=01;35:*.jpeg=01;35:*.gif=01;35:*.bmp=01;35:*.pbm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01;35:*.mkv=01;35:*.webm=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.flv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.axv=01;35:*.anx=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.mid=00;36:*.midi=00;36:*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.axa=00;36:*.oga=00;36:*.spx=00;36:*.xspf=00;36:" "XDG_SESSION_PATH=/org/freedesktop/DisplayManager/Session0" "XDG_SEAT_PATH=/org/freedesktop/DisplayManager/Seat0" "SSH_AUTH_SOCK=/tmp/keyring-XyKrEp/ssh" "SESSION_MANAGER=local/ubuntu:@/tmp/.ICE-unix/4799,unix/ubuntu:/tmp/.ICE-unix/4799" "DEFAULTS_PATH=/usr/share/gconf/ubuntu-2d.default.path" "XDG_CONFIG_DIRS=/etc/xdg/xdg-ubuntu-2d:/etc/xdg" "PATH=/usr/lib/lightdm/lightdm:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games" "DESKTOP_SESSION=ubuntu-2d" "PWD=/home/ubuntu" "LANG=en_US.UTF-8" "MANDATORY_PATH=/usr/share/gconf/ubuntu-2d.mandatory.path" "UBUNTU_MENUPROXY=libappmenu.so" "GDMSESSION=ubuntu-2d" "SHLVL=1" "HOME=/home/ubuntu" "GNOME_DESKTOP_SESSION_ID=this-is-deprecated" "LOGNAME=ubuntu" "XDG_DATA_DIRS=/usr/share/ubuntu-2d:/usr/share/gnome:/usr/local/share/:/usr/share/" "DBUS_SESSION_BUS_ADDRESS=unix:abstract=/tmp/dbus-1zeCZoSrS5,guid=10a6e1e3136d655ec8ff22a000000234" "LESSOPEN=|\040/usr/bin/lesspipe\040%s" "DISPLAY=:0" "XDG_CURRENT_DESKTOP=Unity" "LESSCLOSE=/usr/bin/lesspipe\040%s\040%s" "RUNNING_UNDER_GDM=yes" "COLORTERM=gnome-terminal" "XAUTHORITY=/home/ubuntu/.Xauthority" "_=/usr/bin/tail" } }
<kernel> /sbin/init /bin/sh /usr/sbin/lightdm /usr/sbin/lightdm /usr/sbin/lightdm-session /usr/bin/ssh-agent /usr/bin/dbus-launch /usr/bin/gnome-session /usr/bin/unity-2d-shell /usr/bin/gnome-terminal /bin/bash
file execute /usr/bin/tail
#2012/05/05 11:01:27# profile=3 mode=enforcing granted=no (global-pid=5559) task={ pid=5559 ppid=5423 uid=999 gid=999 euid=999 egid=999 suid=999 sgid=999 fsuid=999 fsgid=999 type!=execute_handler } path1={ uid=0 gid=0 ino=181657 major=7 minor=0 perm=0755 type=file } path1.parent={ uid=0 gid=0 ino=17658 perm=0755 }
<kernel> /sbin/init /bin/sh /usr/sbin/lightdm /usr/sbin/lightdm /usr/sbin/lightdm-session /usr/bin/ssh-agent /usr/bin/dbus-launch /usr/bin/gnome-session /usr/bin/unity-2d-shell /usr/bin/gnome-terminal /bin/bash
file read squashfs:/usr/bin/tail
#2012/05/05 11:01:31# profile=3 mode=enforcing granted=no (global-pid=5576) task={ pid=5576 ppid=5575 uid=999 gid=999 euid=999 egid=999 suid=999 sgid=999 fsuid=999 fsgid=999 type!=execute_handler } path1={ uid=999 gid=999 ino=30677 major=0 minor=8 perm=0600 type=fifo } path1.parent={ uid=999 gid=999 ino=30677 perm=0600 }
<kernel> /sbin/init /bin/sh /usr/sbin/lightdm /usr/sbin/lightdm /usr/sbin/lightdm-session /usr/bin/ssh-agent /usr/bin/dbus-launch /usr/bin/gnome-session /usr/bin/unity-2d-shell /usr/bin/gnome-terminal /bin/bash /bin/bash /bin/ls
file ioctl pipe:[30677] 0x5413
(appendix) Installing Ubuntu + TOMOYO on your hard drive
Configuration and learned policy are only available in the LiveCD, and they are lost if you shutdown your system. Please install the system on your hard drive if you want to use continuously. Please double-click an icon named "Install" on the desktop and follow the instructions. Using LiveCD, you can try TOMOYO Linux without any effects to existing system. But when you install the system on your hard drive, existing OS may be overwritten. Please be careful.
You can save TOMOYO Linux policy using ccs-savepolicy command in root user. The newly saved policy is used from next boot sequence.
For more information
In this tutorial, you have experienced TOMOYO's basic access control functionality. TOMOYO Linux has many features. Please follow the links on the top of this page to utilize TOMOYO Linux more effectively.