Chapter 6: How do I develop policy?
6.1. Patterning temporary files
A particular domain may require many different access permissions to many different resources. Since "Enforcing Mode" allows access to only resources explicitly defined, it is important to cover all necessary resources. To do this, permissions can be patterned. A patterned permission will allow multiple domain policy entries to be shortened into a single entry.
This is particularly important for temporary files due to the variety of single-use pathnames involved. They can either be handled in the manner described below, or handled interactively using the policy editor. For details on handling permissions interactively, see how to Remove redundant entries.
Use tomoyo-findtemp to find pathnames from domain policy that are potentially temporary files:
# /usr/sbin/tomoyo-findtemp < /sys/kernel/security/tomoyo/domain_policy
/etc/mtab.tmp /etc/mtab~ /etc/mtab~2302 /etc/mtab~2328 /etc/mtab~2329 /etc/mtab~2330 /etc/mtab~2331 /etc/mtab~2332 /etc/mtab~2339 /etc/mtab~2383 /halt /selinux/disable /selinux/enforce /selinux/policyvers /tmp/sh-thd-1163110572 /tmp/sh-thd-1163113704 /var/cache/samba/browse.dat. /var/lib/nfs/etab.tmp /var/lib/nfs/xtab.tmp /var/lock/mrtg/mrtg_l
In the example above, "/etc/mtab~numeric" and "/tmp/sh-thd-numeric" can be considered to be temporary files. Thus, patterns can be made for these pathnames.
First, the type of pattern must be considered. The numeric strings here appear to be decimal digits. Thus, the "\$" pattern which matches one or more repetitions of decimal digits can be used. See Wildcard expression rules for a list of possible wildcards.
Use tomoyo-patternize to replace all occurrences of "/etc/mtab~numeric" and "/tmp/sh-thd-numeric" in the domain policy with "/etc/mtab~\$" and "/tmp/sh-thd-\$" respectively:
# /usr/sbin/tomoyo-savepolicy -d | /usr/sbin/tomoyo-patternize '/etc/mtab~\$' '/tmp/sh-thd-\$' | /usr/sbin/tomoyo-loadpolicy -d
If preferred, these patterns can instead be managed in exception policy so that "Learning Mode" will append these pathnames using these patterns:
# echo 'file_pattern /etc/mtab~\$' | /usr/sbin/tomoyo-loadpolicy -e # echo 'file_pattern /tmp/sh-thd-\$' | /usr/sbin/tomoyo-loadpolicy -e
6.2. Patterning file access permissions
Access permissions can be patterned to accommodate for files that are not necessarily accessed in "Learning Mode". For example, the domain policy can be changed to accommodate for web server contents:
|
Before |
After |
|---|---|
|
<kernel> /usr/sbin/httpd allow_read /var/www/html/index.html allow_read /var/www/html/alice/index.html allow_read /var/www/html/alice/page1.html allow_read /var/www/html/alice/page2.html allow_read /var/www/html/alice/image1.jpg allow_read /var/www/html/alice/image2.jpg allow_read /var/www/html/alice/archive/page1.html allow_read /var/www/html/alice/archive/image1.jpg allow_read /var/www/html/alice/archive/page2.html allow_read /var/www/html/alice/archive/image2.jpg allow_read /var/www/html/bob/index.html allow_read /var/www/html/bob/page1.html allow_read /var/www/html/bob/page2.html allow_read /var/www/html/bob/image1.jpg allow_read /var/www/html/bob/image2.jpg allow_read /var/www/html/bob/archive/page1.html allow_read /var/www/html/bob/archive/image1.jpg allow_read /var/www/html/bob/archive/page2.html allow_read /var/www/html/bob/archive/image2.jpg |
<kernel> /usr/sbin/httpd allow_read /var/www/html/\*.html allow_read /var/www/html/\{\*\}/\*.html allow_read /var/www/html/\{\*\}/\*.jpg |
Domain policy can be further simplified by placing directives in the exception policy, such as:
path_group WEB-CONTENTS /var/www/html/\*.html
path_group WEB-CONTENTS /var/www/html/\{\*\}/\*.html
path_group WEB-CONTENTS /var/www/html/\{\*\}/\*.jpg
The following can then be defined in domain policy:
<kernel> /usr/sbin/httpd allow_read @WEB-CONTENTS
6.3. Patterning numeric permissions
Patterns can be used for numeric parameters such as the creation mode of a file.
The following domain policy example permits the domain "<kernel> /sbin/init" to use any ioctl requests for /dev/console:
|
Before |
After |
|---|---|
|
<kernel> /sbin/init allow_ioctl /dev/console 0x5401 allow_ioctl /dev/console 0x5402 allow_ioctl /dev/console 0x540B allow_ioctl /dev/console 0x540E allow_ioctl /dev/console 0x540F |
<kernel> /sbin/init allow_ioctl /dev/console 0-0xFFFFFFFF |
Domain policy can be further simplified by placing directives in the exception policy, such as:
number_group ANY_NUMBER 0-0xFFFFFFFF
The following can then be defined in domain policy:
<kernel> /sbin/init allow_ioctl /dev/console @ANY_NUMBER
6.4. Reviewing gathered permissions
Once you think you have done everything you want to allow Apache to do, run the policy editor and change the profile number to 2.
Note that Apache may have executed some external programs (e.g. /bin/sh, /usr/bin/perl, /usr/lib/sendmail) and thus has some descendent domains. Be sure to change the profile number for all descendent domains as well.
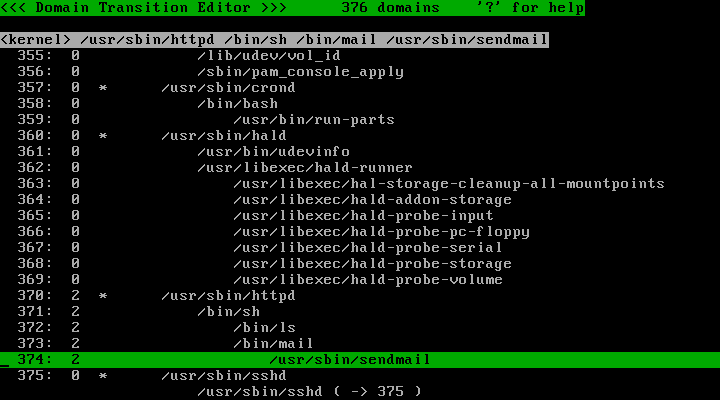
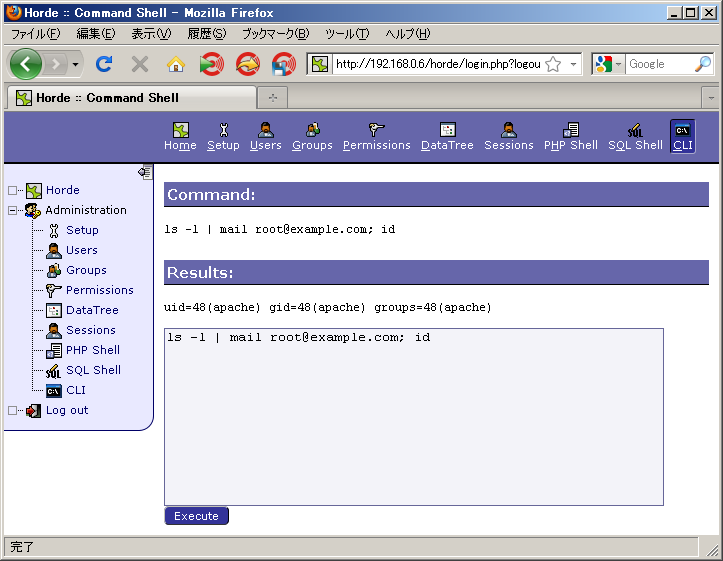
Quit the policy editor and continue using Apache:
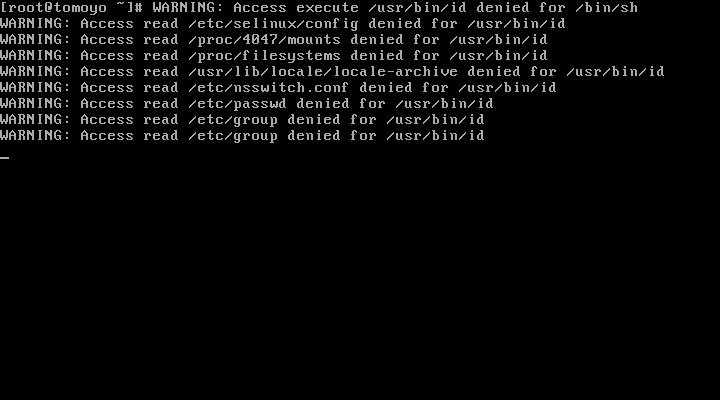
If the profile is configured as "PREFERENCE::permissive={ verbose=yes }" (this is default), the "WARNING:" messages will be printed to the console when policy violation occurs: