Chapter 2: Why do I need TOMOYO Linux?
2.1. What is TOMOYO Linux?
TOMOYO Linux is a Mandatory Access Control (MAC) implementation for Linux that can be used for system analysis or to increase the security of a system. The project was launched in March 2003 and is sponsored by NTT DATA Corporation, Japan. For further technical information, see the SourceForge project page.
TOMOYO Linux 1.x is the original branch of development, which was first released on 11th November 2005 under the GPL. It was implemented as a patch that can be applied to the Linux kernel and is still in active development.
TOMOYO Linux 2.x is the Linux mainline kernel branch of development. In June 2009, a subset of TOMOYO functionality was merged into the Linux kernel 2.6.30 and makes use of standard Linux Security Module (LSM) hooks. However, the LSM hooks must be extended further in order to port the full MAC functionality of TOMOYO Linux 1.x into the Linux kernel. Thus, it does not yet provide equal functionality with the 1.x branch of development. This chart compares the differences between each branch.
This guide is specifically intended for the TOMOYO Linux 2.5.x branch.
2.2. What is Mandatory Access Control?
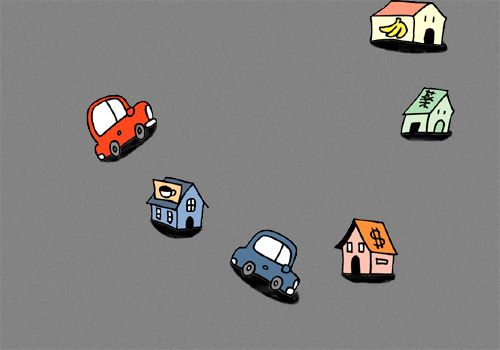
In an operating system (OS), each program or process is mostly unrestricted in the tasks that they are able to perform (see illustration below). A security focused OS should implement some form of restriction that prevents a process from performing tasks that they should not perform, or that the administrator specifically wants to prevent them from performing. For example, a web server such as Apache should be allowed to provide only web services. It should not have access to areas of the filesystem that it does not need, and it should not be allowed to start or interact with other unrelated processes. The Linux filesystem Access Control Lists (ACLs) provide little protection, especially as many services are run as the root user. MAC on the other hand can take this protection much further, allowing very precise control over what each process is allowed to do, even for processes running as root (see illustration below). This is important in the event that a process is compromised. Without MAC, a compromised process would be free to do what it wants!
Unrestricted access on a normal OS:
Restricted access on an OS using MAC:
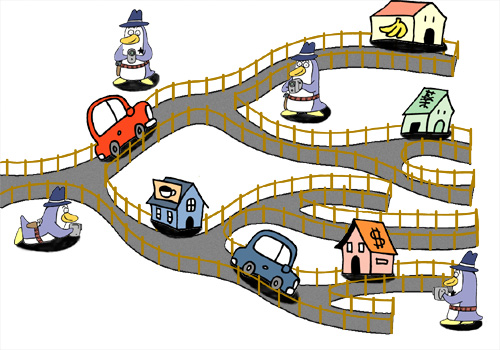
MAC therefore provides a way to create a "policy of least privilege". This is where each process has a definition of what they are allowed to do, which is called the "policy". This policy allows as little as possible for the process to function normally. If a process or application tries to perform a task that is not allowed by this policy, it is denied the ability to perform this task. This prevents any unwanted activity from occurring.
2.3. How can TOMOYO Linux help me?
An important part of MAC is the creation and management of this policy for every process in a system, which requires knowledge of precisely what each process should be allowed to do. This may sound like a fiendishly difficult task and it requires a high degree of understanding and skill. However, TOMOYO Linux provides a "Learning Mode" for automatically generating policy easily and can provide a base from which policy can be developed and refined. This "Learning Mode" can thus be used alongside a firm understanding of the concepts involved in TOMOYO Linux to secure a system in a short amount of time. Any experienced Linux administrator should be able to set up and use TOMOYO Linux within a day!
A restricted system helps to reduce the damage done when an application is compromised. For example, damage can be reduced from security exploits such as buffer overflows. Such protection is therefore especially important for internet-facing services such as Apache or SSH. If a policy of least privilege is in place, a remote attacker that gains control of such an application can be prevented from further compromising a system.